This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Discussions
- NetWitness Community
- Discussions
- Detecting Tor Nodes?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Detecting Tor Nodes?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-10-25 12:33 PM
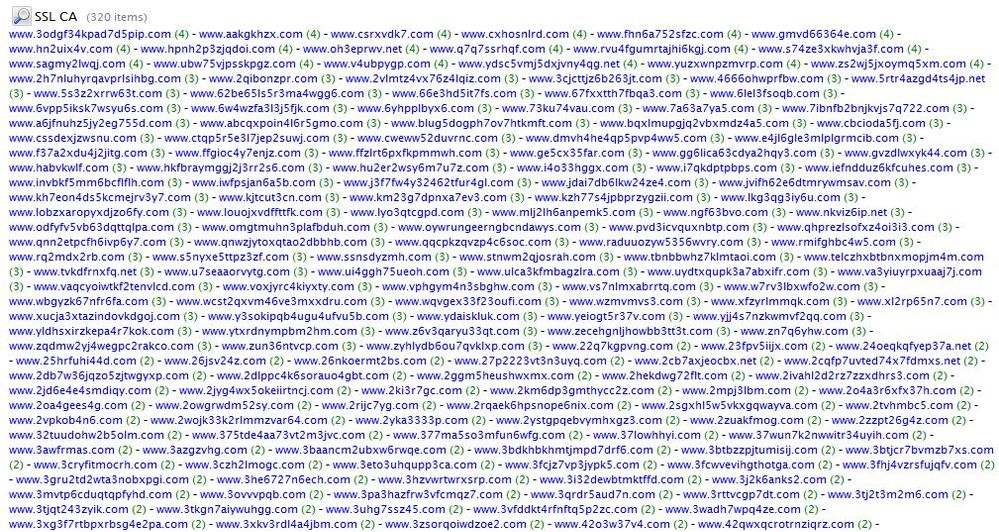
I spend a lot of time looking at a malware sandbox. Today I saw that most, if not all, of the tor connections associated with active malware uses a self signed cert that begins 'www.'
This is what I saw.:
We already have a feed of known tor nodes provided in Live. But by creating an alert rule you can identify possible Undocumented Tor nodes to be investigated. That rule looks like this:
Rule Name: Undocumented Tor Node
Condition: ssl.ca begins 'www.' && threat.source != 'tor-node-ip'
You can test this rule in your own environment by running a custom query. I'm interested to see what other people find in a live enterprise environment?
0 REPLIES 0

© 2022 RSA Security LLC or its affiliates. All rights reserved.