- NetWitness Community
- Discussions
- Re: ECAT Alert on Domain Controller connections
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ECAT Alert on Domain Controller connections
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-17 10:11 PM
Hi All,
I'm not very good at creating ECAT alerts, so I'd appreciate some help in what I'm attempting to achieve.
We have ECAT installed on all our Active Directory controllers, I'd like to generate an alert whenever someone attempts to make a connection to the C$ share.
How would I implement such an alert?
Thanks.
- Labels:
-
RSA NetWitness Endpoint
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-18 04:11 AM
Hi Jeremy,
The approach will have to be slightly different due to the way NWE/ECAT tracks activity. What you would be looking for is this activity towards the DC but not on the DC on the source workstation/server instead.
The attached file which contains both a DB Query and the corresponding IIOC could be adapted for your case. In addition, to the existing criteria you could add a reference to the relevant destination hosts by name or IP in the LaunchArguments_Target field. As in the example below:
AND (
[se].[LaunchArguments_Target] LIKE '%MYDCHOSTNAME%' OR
[se].[LaunchArguments_Target] LIKE '%MYDCIP%'
)
Hope this helps.
Cheers,
Rui
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-21 09:47 PM
Thanks Rui, I think this will be helpful.
Can I ask a more basic question? How do I import/implement this into ECAT?
Is it a simple import using the ECAT UI?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-21 09:54 PM
Another question I had is, does this example only track outbound connections from a host that has ECAT installed, or both incoming and external?
I'm thinking of a case if an attacker would use a host that doesn't have ECAT installed and connects to a DC would that be tracked.
Apologies if it's obvious, I'm still learning the ins and outs of ECAT.
Thanks for your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-22 12:04 AM
Hi Jeremy,
Yes, this would be a simple UI import/creation. You can "Clone" one of the existing Event IIOCs and then just replace the name/description and query with the contents of the file.
You can additionally tweak if you wish to do so just in relation to DCs with the extra lines in the post. We tend to use it at is since C$ and ADMIN$ requires elevated privileges and as per name we are mostly looking for lateral movement.
If you have direct access to the SQL DB you can test it before deploying with the commented out part identified as DB Query to see how effective or noisy this could be in your environment.
Cheers,
Rui
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-22 12:11 AM
It would only track the outbound connections in this case, so if the agent isn't installed on the "attacker" machine you would probably need to be looking at this activity on the "victim/target" hosts.
As a side note, you probably should keep in mind that a lot of this type of activity in large organisations is unfortunately just bad administrator practice and not necessarily malicious. However, normally an attacker would do more that simply just mount a C$/ADMIN$ share, in those cases you should be able to pick other activity on the victim itself via ECAT.
Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-22 12:52 AM
Thanks again for your help, certainly does help.
Bad administrator practice is one thing I'd like to also catch as well as 'bad guys' 😄
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-22 01:50 PM
Hello Jeremy,
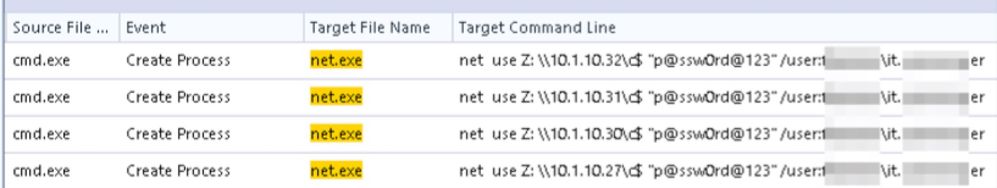
I wanted to complement some of the replies that Rui has already provided. The mounting of shares (c$, admin$, and ipc$) is a typical step of lateral movement. Typically, or at some point, this will happen from an endpoint in the network that will hopefully have ECAT deployed. In such cases these events are very obvious and something that you should monitor daily. Like Rui mentioned, not all share mounting events are malicious, and so you will need to filter out those that are common in your network. Below is an example of what this event would look like. Namely, it would be a Create Process Event where the source filename will be cmd.exe and the target filename net.exe. You typically also get to see what account the attacker is using for lateral movement, as it is specified in the arguments along with its password:
You are also correct to wonder what happens if the attacker runs these commands from a system that does not have ECAT in it (whether it is an attacker system, or an endpoint in the network that does not have an ECAT agent installed). In such cases, if the remote share mounting is done for the purpose of copying files to/from the target system (such as your DC), then it depends what types of files these are. I say this because of the types of events we report with ECAT, i.e., ECAT is primarily focused on modules (PE files, and scripts).
In other cases our team has worked, we have seen attackers use tools like wmiexec.py (impacket/wmiexec.py at master · SecureAuthCorp/impacket · GitHub ) that leave artifacts such as \\127.0.0.1\ADMIN$\__1619916855.94 2>&1 in the target system where ECAT is running:
cmd.exe /Q /c powershell -c "$K='OMITTED BASE64 DATA';$i=0;[char[]]$b=([char[]]([System.IO.F ile]::ReadAllBytes('c:\windows\mswdrt.dat')))|%{$_-bXor$k[$i++%$k.Length]};IEX ($b-join''); Invoke-Mimikatz -DumpCreds; Invoke-Mimikatz -Command 'privilege::debug token::elevate lsadump::sam'; del c:\windows\msdrt.dat" 1> \\127.0.0.1\ADMIN$\__1619916855.94 2>&1
Please be mindful that the code for this tool can be easily modified and that this is just an example of the default version of this tool.
When creating an IIOC to detect this type of activity you can either look for signs of \admin$ in the command line or you can keep things even more generic and just look for the STDOUT/ERR redirect "2>&1". Attached is a template IIOC that can help you detect such activity. The IIOC includes the DB query which is useful to filter out all the legitimate activity in your environment, prior to mimicking that logic in the IIOC code itself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-01-22 07:58 PM
Thanks for your input Hermes, I'll take a look at your template, appreciate the help.
J.