- NetWitness Community
- Discussions
- Re: EPL RULE - Lockouts
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
EPL RULE - Lockouts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-18 12:36 PM
Hello,
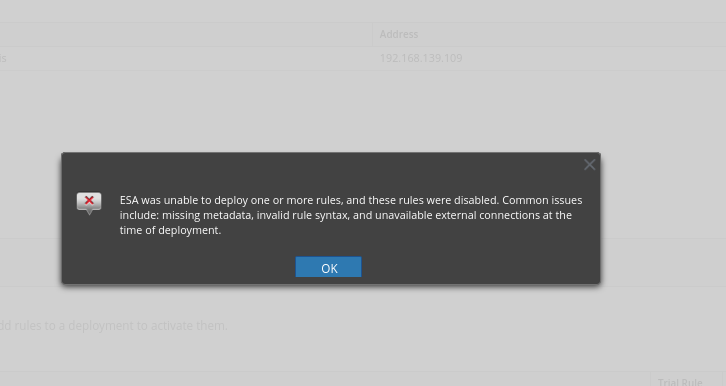
I was trying to build a rule to group by device host and user the multiple account lockouts but after deployed it doesnt work and stays disabled.
@RSAAlert(oneInSeconds=0, identifiers={"user_dst"})
SELECT * FROM
Event( ( (ec_subject='User' AND ec_activity='Lockout')
OR
(device_class = 'Windows Hosts' AND reference_id IN ('4740', '644')) )
AND
medium = 32
AND user_dst IS NOT NULL
AND device.host IS NOT NULL
).win:time_length_batch(600 sec, 10) HAVING COUNT(*) = 10; ).std:groupwin(user_dst).win:time_length_batch(60 seconds, 10) GROUP BY user_dst and device.host HAVING COUNT(*) = 10;
Can anyone help me?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-18 01:43 PM
any debug logs? switch to the admin view, locate ESA, Locate logs, Locate the logs for that rule in the history tab and see if that tells you why it failed to deploy.
post them here when you find them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-18 02:29 PM
Try replacing the underscore in device.host as 'device_host' for it to be recognized by ESA, update the group by to be comma-separated 'GROUP BY user_dst, device_host' and remove the duplicate time window.
@RSAAlert(oneInSeconds=0, identifiers={"user_dst"})
SELECT * FROM
Event( ( (ec_subject='User' AND ec_activity='Lockout')
OR
(device_class = 'Windows Hosts' AND reference_id IN ('4740', '644')) )
AND
medium = 32
AND user_dst IS NOT NULL
AND device_host IS NOT NULL
).win:time_length_batch(60 seconds, 10) GROUP BY user_dst, device_host HAVING COUNT(*) = 10;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-18 03:08 PM
i thank both of you for the help,
i tried what you said Angela but still doesn't work
Eric,
How can i do that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-18 04:05 PM
Within the UI go to ADMIN > Services, select your ESA service and then View > Logs. In the filter dropdown, select the WARN message type and you should see deployment error messages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-28 09:41 AM
Hello Angela,
Luckily the rule was deployed when i tried another time, but unfortunelly ii only creates alerts not incidents....
Is there anything i must do in the EPL rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-05-29 12:04 PM
There is a default Incident Rule to aggregate on all high severity ESA rules called 'High Risk Alerts: ESA'. You could decrease the risk setting within the Incident Rule, increase the risk on the ESA rule to match the setting within the existing Incident Rule or create your own custom Incident Rule as needed. See the RSA Link reference page: Respond Config: Aggregation Rules Tab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-06-04 05:58 PM
I already did that....but now i dont have any incident and no alert:
Im using this
SELECT * FROM
Event(
medium = 32
AND
ec_activity = 'Logon'
AND
ec_theme = 'Authentication'
AND
ec_outcome = 'Failure'
AND
(ip_src IS NOT NULL OR device_ip IS NOT NULL)
AND
user_dst IS NOT NULL
AND
device_host IS NOT NULL
).std:groupwin(device_host, user_dst).win:time_length_batch(180 seconds, 3).std:unique(user_dst) GROUP BY user_dst, device_ip, device_host HAVING COUNT(*) = 3;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-06-11 02:56 PM
Does anyone knows whats happening with the rule?
I still cant get any incident....