- NetWitness Community
- Discussions
- ESA Alert Template Raw log possible ? CEF
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ESA Alert Template Raw log possible ? CEF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-31 07:02 AM
Hello,
We are tying to send in syslog esa alert to Archer.
Is there a way to send the raw log, who have trigerred the alert to archer ? I know how to sent meta like our template below, but we need to send all the log.
<#list events as x>CEF:0|RSA|Security Analytics (ESA)|10.3.3|20|This incident is based on the rule "${moduleName}" and based on the aggregation criteria "Destination User" where the Destination User is:${x.user_dst!" "} and source is:${x.host_src!" "} and destination is:${x.alias_host!" "} and Port source is:${x.ip_srcport!" "} and Ports destination is:${x.ip_dstport!" "} |3|externalId=${x.sessionid!" "} src=${x.host_src!" "} dst=${x.alias_host!" "} rt=${time?datetime} sourceServiceName=${x.service!" "} requestClientApplication=${x.client!" "} destinationDnsDomain=${x.domain_dst!" "} smac=${x.eth_src!" "} dmac=${x.eth_dst!" "} cs1=${x.city_dst!" "} cs1Label=destinationcity cs2=${x.country_dst!" "} cs2Label=destinationcountry cs3=esa-${moduleName}-${x.user_dst!" "} cs3Label=aggregationcriteria alertagg=${id} cs4=${x.did!" "} cs4Label=decoderid cs5=${x.cid!" "} cs5Label=concentratorid cs6=${x.threat_source!" "} cs6Label=threatsource cs7=${x.referer!" "} cs7Label=referer cs8=esa cs8Label=RCFApplicationName spt=${x.tcp_srcport!" "} dpt=${tcp_dstport!" "} cs9=${x.udp_srcport!" "} cs9Label=udpsourceport cs10=${x.udp_dstport!" "} cs10Label=udptargetport cs11=${x.latdec_dst!" "} cs11Label=destinationlattitude cs12=${x.latdec_src!" "} cs12Label=sourcelattitude cs13=${x.longdec_dst!" "} cs13Label=destinationlongitude cs14=${x.longdec_src!" "} cs14Label=sourcelongitude cs15=${x.alert_id!" "} cs15Label=alertid cs16=${x.domain_src!" "} cs16Label=sourcedomain cs17=${x.domain_dst!" "} cs17Label=destinationdomain cs18=${moduleName} cs18Label=alert cs19=${x.country_src!" "} cs19Label=sourcecountry cs20=${x.city_src!" "} cs20Label=sourcecity cs21=${x.device_id!" "} cs21Label=deviceid msg=${moduleName} grouped by Destination User:${x.user_dst!" "} cs24=${x.risk_info!" "} cs24Label=riskinfo cs25=${x.risk_warning!" "} cs25Label=riskwarn cs26=${x.risk_suspicious!" "} cs26Label=risksusp cs27=${x.threat_category!" "} cs27Label=threatcategory cs28=${x.threat_desc!" "} cs28Label=threatdesc cs29=L2 Incident Handlers cs29Label=Incident_Queue cs30=Automatic cs30Label=Detection_Type cs31=Abnormal activity cs31Label=Incident_Type_1 cs32=Network cs32Label=Category cat=${x.category!" "} level=${x.level!" "} devicetype=${x.device_type!" "} deviceclass=${x.device_class!" "} suser=${x.user_src!" "} eventsource=${x.event_source!" "} eventtype=${x.event_type!" "} eventdescription=${x.event_desc!" "} duser=${x.user_dst!" "} filename=${x.filename!" "} deviceip=${x.device_ip!" "} esaseverity=${severity} time=${x.esa_time?number_to_datetime!" "} statement=${statement} id=${id} moduleType=${moduleType}$$$$</#list>
Regards,
Clement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-31 08:17 AM
Hi Clement,
I have moved this thread to the https://community.rsa.com/community/products/netwitness?sr=search&searchId=e4e4077a-00bb-499f-8485-a421540563cc&searchIndex=0 community so that you can get an answer to your question.
Thanks,
Jeff
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-31 02:33 PM
Hi Clement,
You have a couple options to figure out which metakeys and metavalues are in the raw alert.
The first is to look at the raw alert and use that that to modify your template to include the meta that you find there. The other option is to simply add every single metakey you have within your NetWitness environment.
FWIW, I think the second option here is a better overall choice as it will likely require less management of ESA templates as a whole. There will be a larger initial time investment to create a template with every metakey in your environment, but once created you would only need to update that template if / when you add new metakey definitions to your index-<service>-custom.xml files.
If you go with the first option, depending on what version of NetWitness you're on, you'll be able to find the raw log in one of two places.
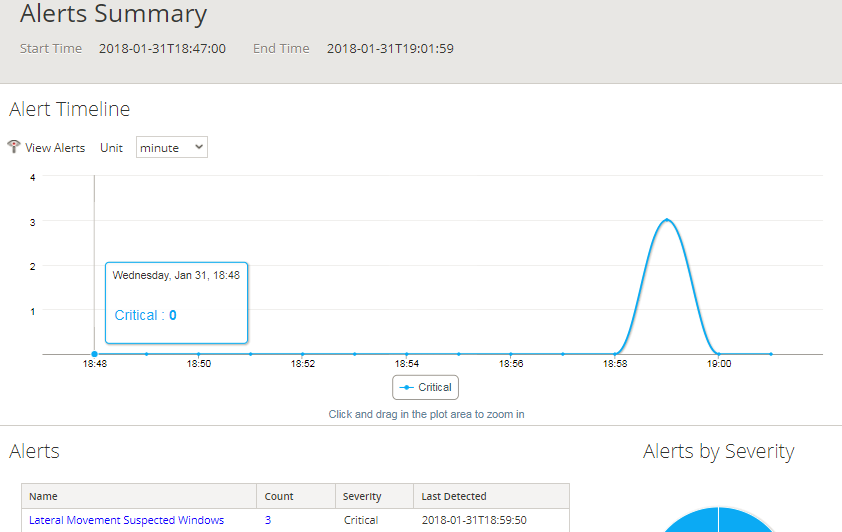
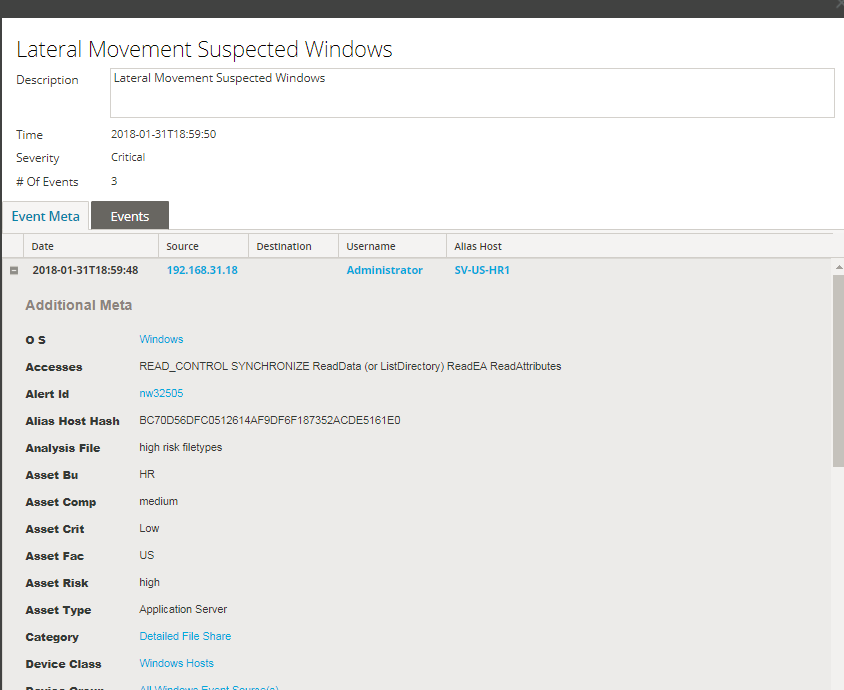
If you're on 10.6.x, browse to Alerts --> Summary, click into any of your existing ESA alerts, and then double-click on any of the events in that list. You can then expand the field within the Event Meta tab to view all the meta associated with the events that triggered the alert:
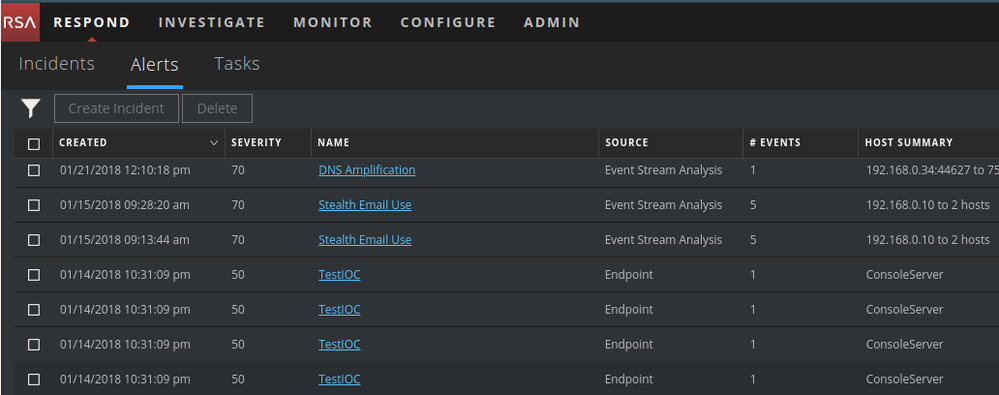
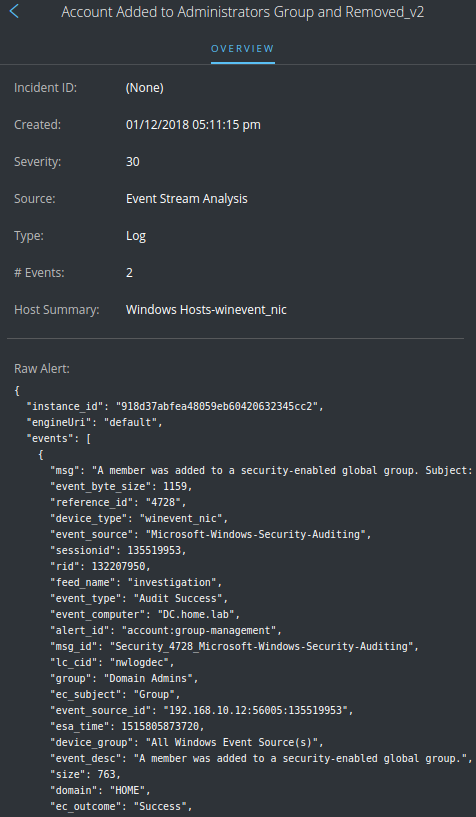
If you're on 11.x, raw alerts can be viewed within the Respond module at Respond --> Alerts and then by selecting any of the Alerts present. The raw alert contents will appear in a sidebar to the right if you simply select an alert, or in a sidebar to the left if you click into an alert:
You can then use these details to know which meta exist for any particular alert and adjust your alert template accordingly.
Hope this helps.
Mr. Mongo