- NetWitness Community
- Discussions
- Re: How do I enter an IP range in EPL using RegEx?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How do I enter an IP range in EPL using RegEx?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-11 06:54 AM
Hello everybody,
I hope you can help me out.
I have created a rule in EPL that should trigger whenever the corresponding event occurs in one of the metafields. I would also like to receive an alarm if a certain IP range occurs. In order not to list the entire IP range, I would like to use RegExp here. Can either of you tell me how to integrate RegExp into my rule?
My code looks like this, but unfortunately I get a syntax error:
SELECT * FROM
Event(
medium = 32 AND
ec_activity = 'Logon' AND
ec_theme = 'Authentication' AND
ec_outcome = 'Failure' AND
result = 'failed publickey' AND
(matchRegex(device_ip, "(10\.169\.([0-9]|[1-9][0-9]|1([0-9][0-9])|2([0-4][0-9]|5[0-5]))\.([0-9]|[1-9][0-9]|1([0-9][0-9])|2([0-4][0-9]|5[0-5])))")) AND
user_dst IS NOT NULL AND
host_src IS NULL
).std:groupwin(user_dst_hash , device_ip , device_host).win:time_length_batch(120 seconds, 3) GROUP BY user_dst_hash , device_ip , device_host HAVING COUNT(*) = 3;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-11 09:29 AM
Hi Hidayat,
I have moved this thread to the RSA NetWitness Platform" data-type="space so that you can get an answer to your question.
You can post future questions and discussions directly to that community by clicking on the Ask a Question or Start a Discussion button on the RSA NetWitness Platform" data-type="space page.
Thanks,
Jeff
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-11 12:53 PM
Hi Hidayat,
You are looking to match against anything in the 10.169.0.0/16 range, yes?
One issue with your match statement - it will not match against the full 0-255 range in the last octet, only against the first digit in the octet.
For example:
10.169.255.1 à this would match fully
10.169.255.100 à this would match only to "10.169.255.1”
10.169.255.255 à this would match only to "10.169.255.2”
You can fix this by either adding string beginning (^) and string end ($) tokens to your regex:
(^10\.169\.([0-9]|[1-9][0-9]|1([0-9][0-9])|2([0-4][0-9]|5[0-5]))\.([0-9]|[1-9][0-9]|1([0-9][0-9])|2([0-4][0-9]|5[0-5]))$)
Or by using a different regex that does not need them:
(10\.169\.[0-9]{1,3}\.[0-9]{1,3})
A second potential issue I see with the rule is that you are grouping by user_dst_hash. If you have not set up data obfuscation on the user.dst meta key, then user.dst.hash meta will not be available for ESA. I'd recommend you double-check that meta is available in ESA.
Lastly - if you want to group by distinct user.dst values, you could change your grouping statement to:
.std:groupwin(device_ip , device_host).win:time_length_batch(120 seconds, 3).std:unique(user_dst) GROUP BY device_ip , device_host HAVING COUNT(*) = 3
Let us know if this works for you.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-12 12:43 AM
On top of Jashua's recommendations.
https://community.rsa.com/docs/DOC-85694 document might help on ip regex for EPL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-18 07:27 AM
Hi Joshua,
I was very grateful for your quick support, thank you very much.
Your help was great, the EPL-"compiler" doesn't report a syntax error anymore. Right now, I'm testing to see if the rule works. ![]()
Kind regards
Hidayat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-18 07:31 AM
Hi Sravan,
thanks for your help and the nice tip. ![]()
Kind regards
Hidayat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-04-19 10:39 AM
Hi Joshua,
everything's working fine. Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-07-12 10:51 AM
Hi Joshua,
Just to test the internal traffic, have created below, rule is saved but not thoroughing any alert. Don't know what's wrong here. Your suggestions will be highly appreciated!
@Name('test-internal')
@RSAAlert(oneInSeconds=0)
SELECT * FROM Event
(
device_class IS NOT NULL
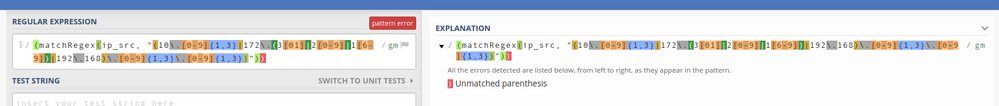
AND (matchRegex(ip_src, "(10\.[0-9]{1,3}|172\.(3[01]|2[0-9]|1[6-9])|192\.168)\.[0-9]{1,3}\.[0-9]{1,3})"))
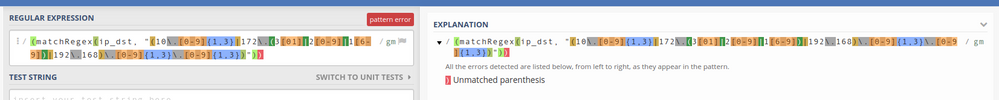
AND (matchRegex(ip_dst, "(10\.[0-9]{1,3}|172\.(3[01]|2[0-9]|1[6-9])|192\.168)\.[0-9]{1,3}\.[0-9]{1,3})"))
)
.std:groupwin(ip_src, ip_dst)
.win:time_length_batch(60 seconds, 200)
GROUP BY ip_src, ip_dst
;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-07-12 01:23 PM
Though not an answer for using regex for an IP range in EPL, I highly suggest tagging any IP ranges using either a Feed or Application Rule on the Decoders (Log, Network or Endpoint), some of this may already be done if you have configured the traffic_flow_options.lua file to recognize your internal networks, they would then be tagged in both the 'netname' key buy "name src" or "name dst" and the 'direction' key for "inbound","outbound", & "lateral"
Let the decoders do the heavy lifting instead of making complex regex like queries in EPL, it's more efficient.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-07-12 01:40 PM
Hi Deepak,
I highly recommend https://regex101.com/. I think I’ve used that tool for pretty much every single regex I’ve ever written.
A simple copy/paste of your matchRegex statements into regex101 shows that you have an unmatched parenthesis at the end of each:
This is caused by a right parenthesis ")" in the middle of your regex (after the 192\.168\.) that should not be there.
That said, I'll echo what John Snider says below about using feeds and/or app rules and/or the traffic_flow_options.lua file to tag your ip ranges with meta and use that meta in your ESA rules. Let your decoders do as much of the heavy lifting as you can.
Mr. Mongo