- NetWitness Community
- Discussions
- How to Create a Custom Feed in 10.2 SP2
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Create a Custom Feed in 10.2 SP2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-09-26 10:15 AM
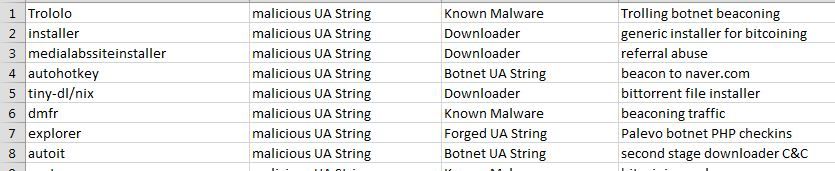
I have a list of over 130 known malicious user-agent strings that can identify known botnet beaconing, backdoor installers, and poorly coded malware that identifies itself because the malware author chose a unique and identifiable user-agent string that makes it stand out on a network. If you would like to use this list, you can install it yourself as a feed. It is attached to this post below. Save the .CSV file to your local system and then follow the screenshots and instructions below to install this content. The process should help you get familiar with the feed wizard and give you confidence to create your own feeds.
About the CSV- Column 1 is intended to be my indexed values. Column 2 is my feed.name, Column 3 is a feed.category and Column 4 is my feed.description. The feed.description is a simple note to tell me why we think the entry in Column 1 is malicious. Note that you do not need column headers in the CSV.
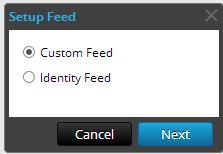
There is an easy way to get your feed values loaded into the system. Navigate in SA to Live and then Feeds to create a new custom feed using the feed wizard. Click the Plus sign to add a new custom feed.
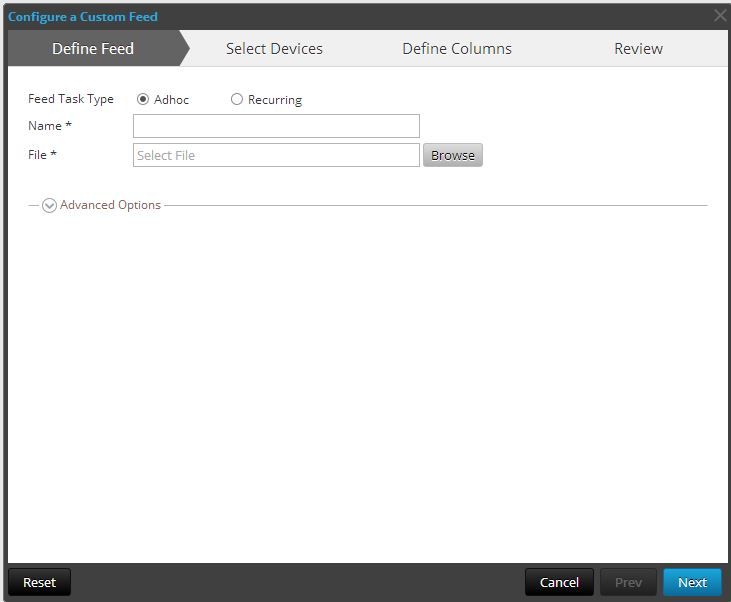
Select the AdHoc radio button and name the feed. Then browse to your copy of the CSV that you downloaded from the attachment below.
After pressing next, you select your target decoders to host the feeds. Then hit next again.
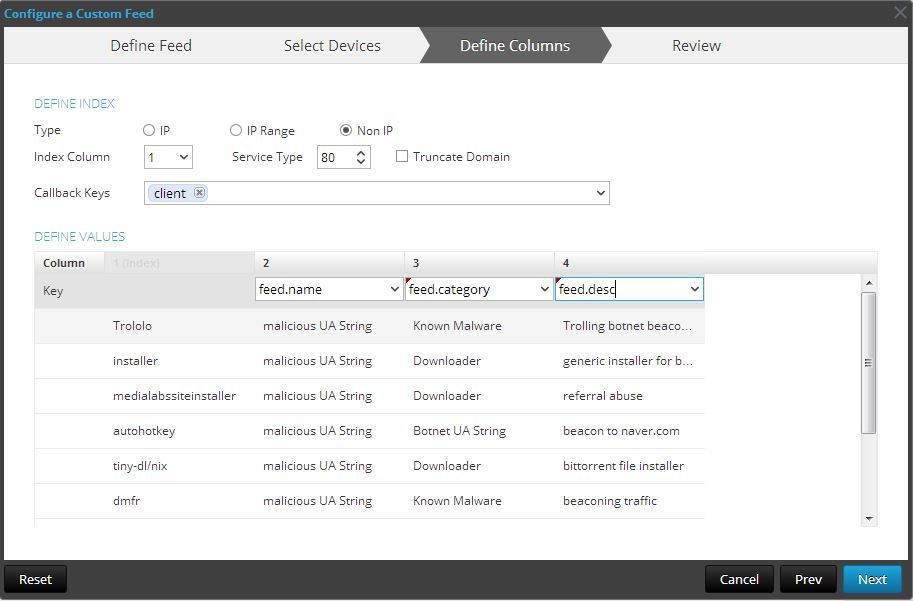
You need to define the index and the type of feed. This is a Non IP feed, so click that radio button. Our feed values are in column 1, so select column 1 as the Index Column. Since we are talking about User-Agent strings, which is web based, select service type 80. And since User-Agent strings populate the Client key in Security Analytics, we will select Client from the Callback Keys field.
Select feed.name for Column 2, Feed.Category for Column 3, and Feed.Desc for Column 4.
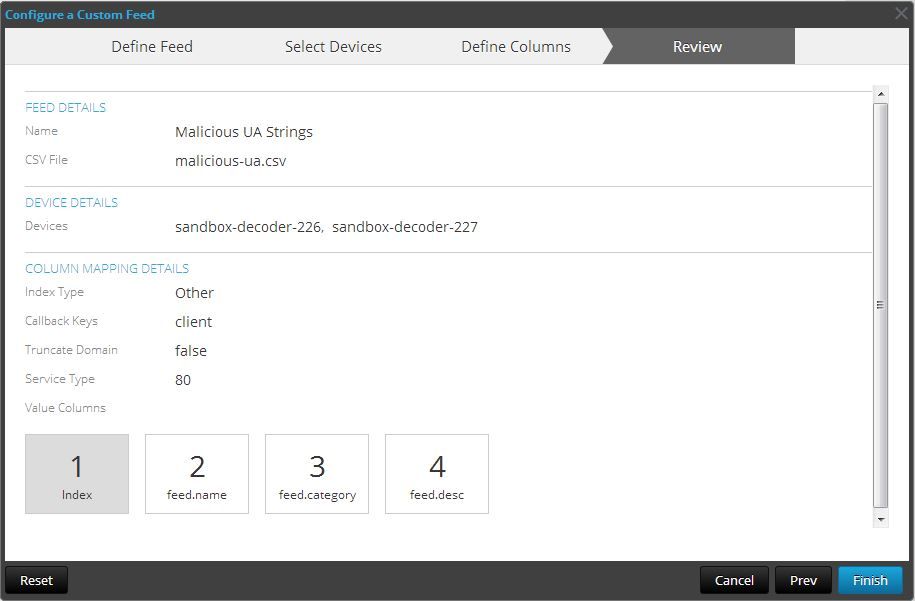
After clicking next, the review screen will ask that you confirm your settings.
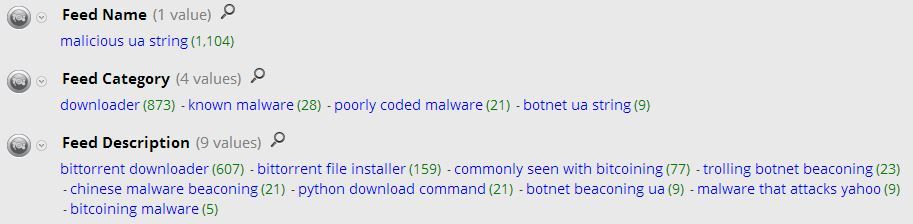
And then you click finish, and the feeds will deploy to the decoders. The addition of a new feed should automatically signal your feed parser to reload. Here are what the results look like in my environment, which is mostly pure malware.
You can now setup alerts in Reporter to identify the existence of any meta in the above keys.
It should be noted that if you wish to add your own malicious UA strings to this feed, you can do so manually by updating the CSV and then reloading it using the same wizard above. In fact, to test if your feed will work, and these client strings are pretty rare, you may wish to add a more popular and benign user-agent string to column 1 to make sure the feed is firing.
I hope following this example process will help you be comfortable with implementing your own feeds to support your use cases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-06-23 12:59 PM
Very helpful and really well-written. Thanks!