- NetWitness Community
- Discussions
- Re: How to Detect Botnet Beaconing That is Blocked By Your Firewall
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Detect Botnet Beaconing That is Blocked By Your Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2012-09-04 01:36 PM
NetWitness NextGen can actually detect compromised endpoints on your network by detecting connection attempts to known Command and Control servers- connection attempts that are being blocked by your firewall or smart proxy. Also, if known C&C hosts get blackholed, those bots out there will still try to communicate, and we can see these. Here's how you do it.
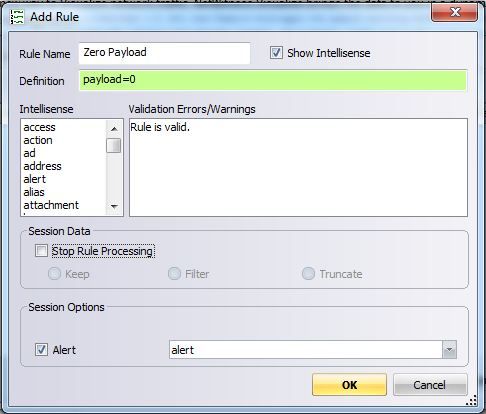
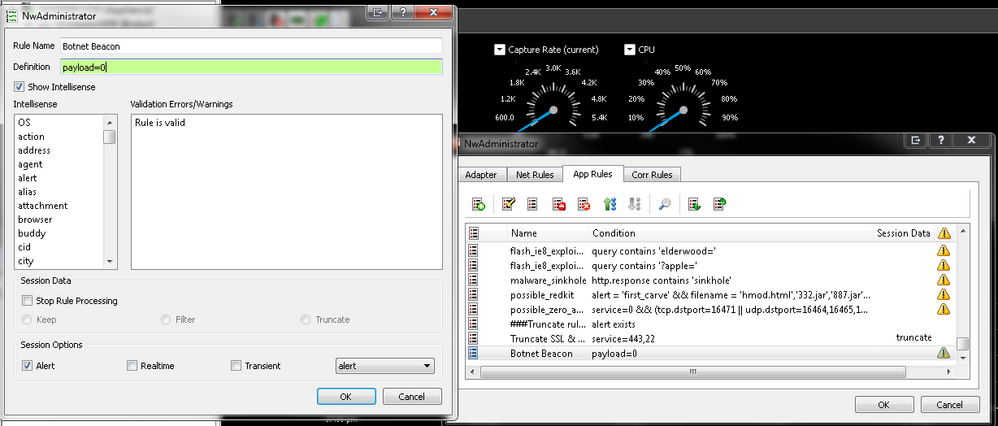
- Step 1: Deploy Zero Payload Rule. Create a rule on the decoders to identify packets that have zero payload. The rule should be called "Zero Payload" with the contents of the rule simply being "payload=0" Deselect the option to stop rule processing and set the rule to alert into the Alert field. Packets such as this are typically SYN connections.
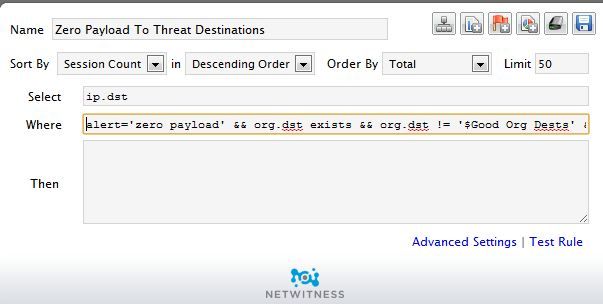
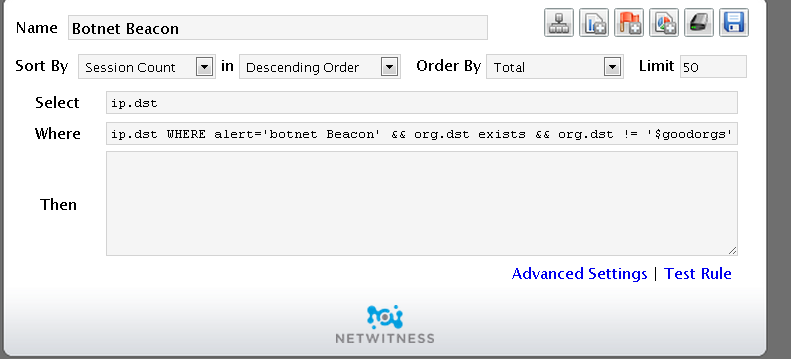
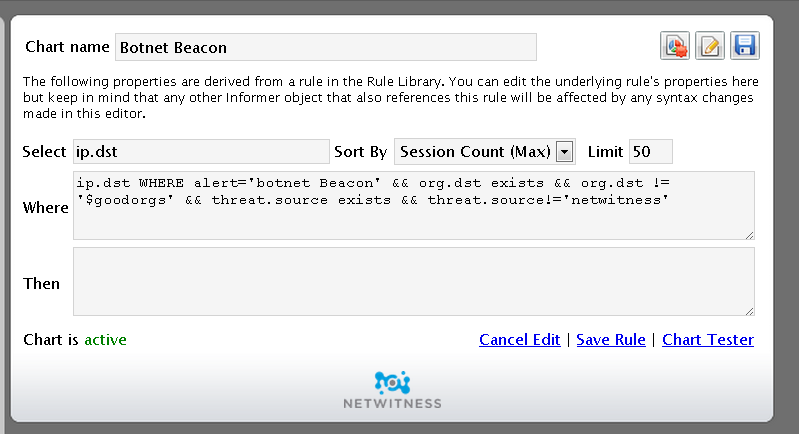
- Step 2: Create an Informer Chart. Create a chart in Informer that looks for instances of this rule firing to all destination IP addresses that are listed in our 3rd party Threat Feed lists. The rule for this chart should look for
ip.dst WHERE alert='zero payload' && org.dst exists && org.dst != '$goodorgs' && threat.source exists && threat.source!='netwitness'
and turn that rule into a chart. Track the top 15 items.
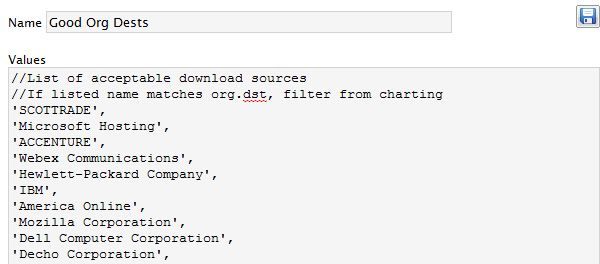
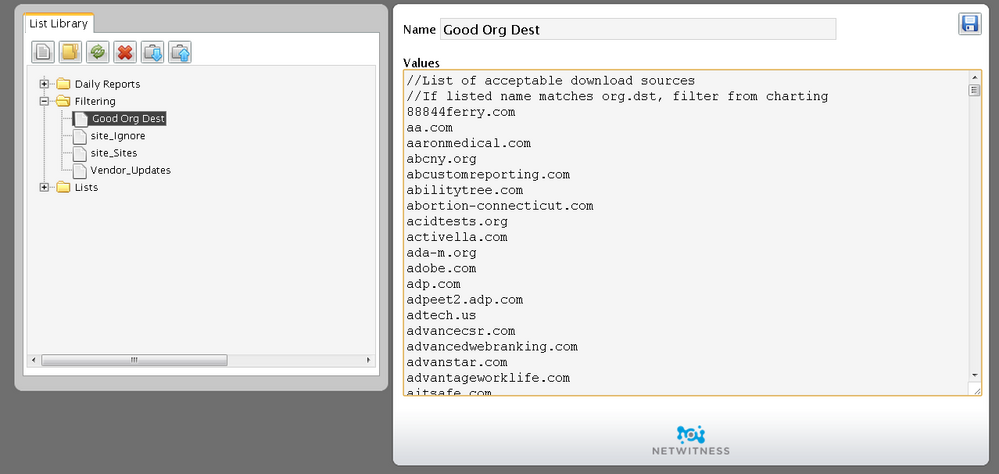
- Step 3: Create your white list of known good destination organizations. As you begin investigating the results of this chart and rule you will invariably find known IP destinations that are trusted. Like Google, a host in a common CDN, etc. Add these destination organizations to this whitelist referenced in the rule of Step 2.
When deployed in the field, I typically see several connection attempts to known bad destinations. And since it is a chart, you will begin to see the timed pattern of the traffic as well. What this usually represents is a compromised source IP address that is attempting to connect to a blocked or blackholed destination, or you have orphaned malware that is trying to call home. Those sources should be pulled from the network for re-imaging or similar internal IR process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2012-09-07 12:40 PM
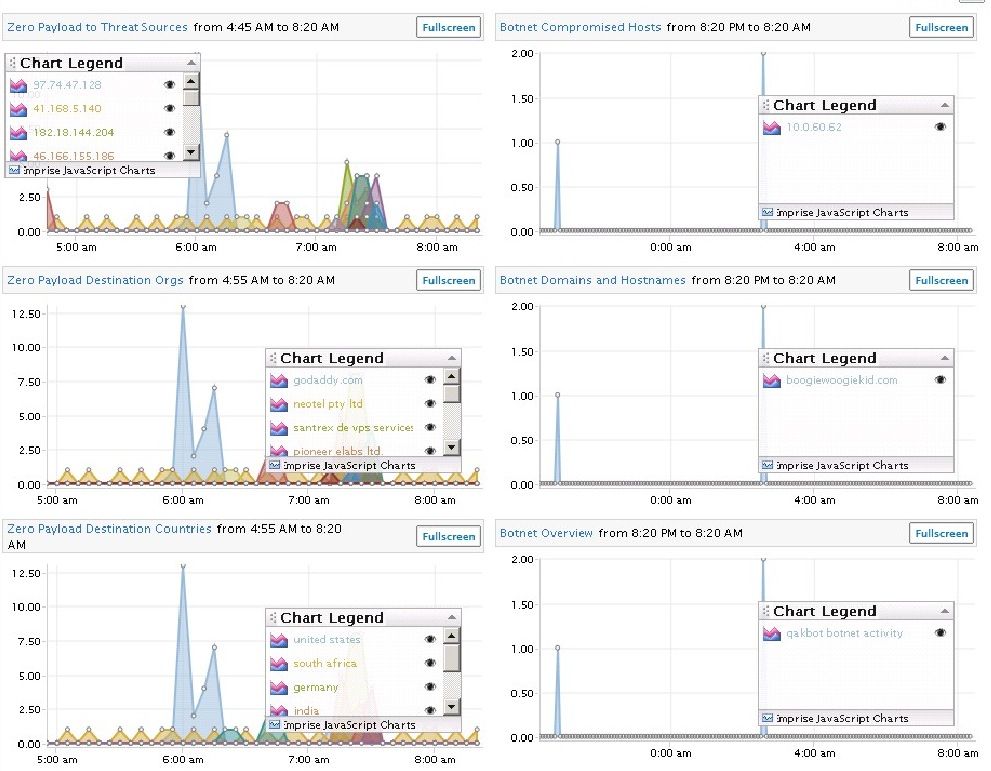
The below dashboard in Informer shows all botnet activity in an organization. Click the image to see the full size. The stacked charts on the left show the Zero payload activity going to three distinct meta elements: the destination IP, the destination organization and the destination country. Taken together, an analyst can instantly understand all of the meta surrounding the zero payload packets attempting to go outside of the organization.
Notice the distinct orange beaconing pattern to 41.168.5.140? According to a simple Google Search, this activity is associated with a malicious PDF trojan. The link takes you to Wepawet's analysis of the malware. We didn't see the initial infection, but it is clear the source IP is compromised and needs remediation.
The right hand stack of charts shows our botnet parsers detecting payload of qakbot activity to a known bad destination. With both stacks of charts on the dashboard, an analyst has instant, realtime access to his enterprise's botnet activity, regardless of the payload.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 11:54 AM
Hi,
I had a question in regards to this rule/chart.
I followed what you said above, but I cannot get this to work.
I am getting no results on the Dashboard.
There were a few things I was not sure of along the way, so maybe that's the issue.
I added an App rule in the Decoder(I'm assuming it was an App rule) as stated above.
I did not call it Zero Payload tho, as we already had a rule created with that name when PS came in here to set things up.
Instead I have called it Botnet Beacon and have made the change in your query line as well to that name:
ip.dst WHERE alert='botnet Beacon' && org.dst exists && org.dst != '$goodorgs' && threat.source exists && threat.source!='netwitness'
I added this to the rule and chart in Informer as well.
I was unsure where to do the whitelist so I added it to the List Library.
Maybe that's my issue?
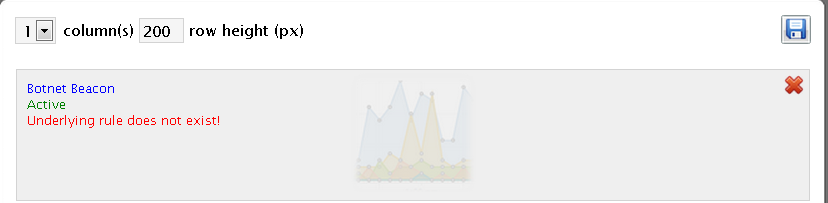
I am also getting this error below when I look Define Dashboards.
I see the rule but am not sure why I am getting this.
I am still new to this so I am sure I missed something somewhere.
Any help would be appreciated.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 12:09 PM
You need to remove "ip.dst WHERE" from both your Where: clause statements. Making them only:
alert='botnet Beacon' && org.dst exists && org.dst != '$goodorgs' && threat.source exists && threat.source!='netwitness'
Hope that helps!
Regards,
Rui
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 12:17 PM
Hi Rui,
I just tried it but it still shows no results.
Plus I am still getting that error when I look Define Dashboards.
thanks ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 12:31 PM
Ah! Yes, just noticed that your list name is different on the definition of the list and the rule, they need to be the same.
Also it seems like you have domain names instead of organization names, look on investigator for the "Destination Organization" value or use a simple report with
Select: org.dst
Where: org.dst exists
If you get the top 10 or so organizations you should see the most common for your environment.
Apologies, I didn't look through it all in detail once I noticed the previous issue.
Hope that helps!
Rui
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 12:43 PM
Also, watch your capitalization. Your Informer rule is looking for 'botnet Beacon'. Should just be 'botnet beacon'
Also, wait until you start getting results before you filter things out in your whitelist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 12:44 PM
Oh, and those lists are only good for up to 100 meta elements. You probably won't have to filter more than a dozen "good orgs"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 01:45 PM
Rui, Fielder,
It looks like my list wont work with this, if the limit is 100.
The list I am using is the same list we use with the firewall and that list has 1700+ names on it.
If this 100 is the limit, then I will have to save this for when I have time to get it down to 100 names.
Thanks guys.. really appreciate your guidance with everything.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-18 01:50 PM
Org.dst is different than alias.host. Leave your list empty for now and put in org.dst based on results of your analysis based on results. I guarantee you won't ever need to exceed 100 orgs.