- NetWitness Community
- Discussions
- Re: How to Detect Botnet Beaconing That is Blocked By Your Firewall
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Detect Botnet Beaconing That is Blocked By Your Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2012-09-04 01:36 PM
NetWitness NextGen can actually detect compromised endpoints on your network by detecting connection attempts to known Command and Control servers- connection attempts that are being blocked by your firewall or smart proxy. Also, if known C&C hosts get blackholed, those bots out there will still try to communicate, and we can see these. Here's how you do it.
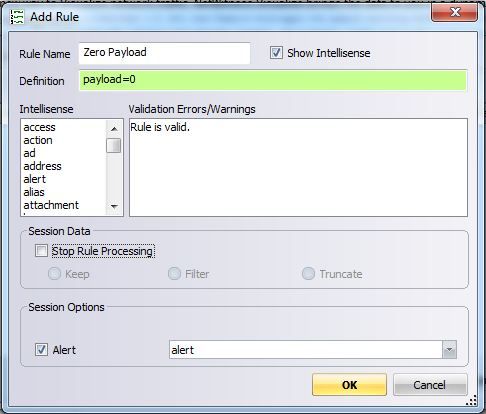
- Step 1: Deploy Zero Payload Rule. Create a rule on the decoders to identify packets that have zero payload. The rule should be called "Zero Payload" with the contents of the rule simply being "payload=0" Deselect the option to stop rule processing and set the rule to alert into the Alert field. Packets such as this are typically SYN connections.
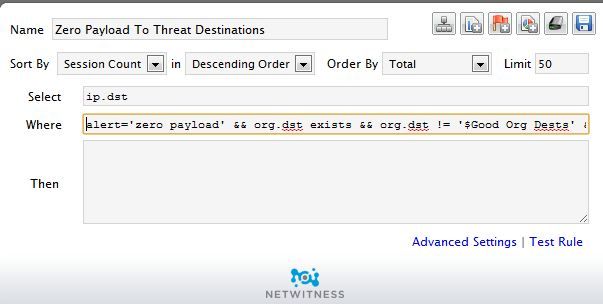
- Step 2: Create an Informer Chart. Create a chart in Informer that looks for instances of this rule firing to all destination IP addresses that are listed in our 3rd party Threat Feed lists. The rule for this chart should look for
ip.dst WHERE alert='zero payload' && org.dst exists && org.dst != '$goodorgs' && threat.source exists && threat.source!='netwitness'
and turn that rule into a chart. Track the top 15 items.
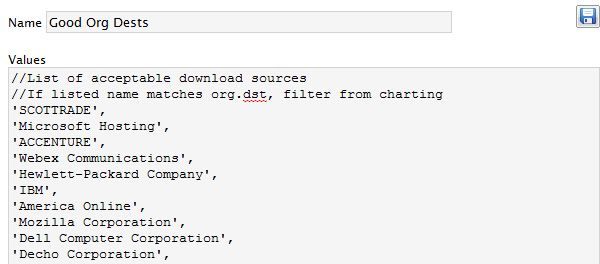
- Step 3: Create your white list of known good destination organizations. As you begin investigating the results of this chart and rule you will invariably find known IP destinations that are trusted. Like Google, a host in a common CDN, etc. Add these destination organizations to this whitelist referenced in the rule of Step 2.
When deployed in the field, I typically see several connection attempts to known bad destinations. And since it is a chart, you will begin to see the timed pattern of the traffic as well. What this usually represents is a compromised source IP address that is attempting to connect to a blocked or blackholed destination, or you have orphaned malware that is trying to call home. Those sources should be pulled from the network for re-imaging or similar internal IR process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-19 12:09 PM
Hi Rui,
That Zero Payload does work but I am not sure what the difference between these 2 would be, which is what I was curious about.
This is the rule for it:
| Select | org.dst |
| Where | alert='zero_payload' |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-19 12:16 PM
Probably the " " versus the "_" or maybe the location of the rule in the list, the rules are evaluated sequentially and there are some rules that will cause the evaluation to stop. Namely, filter and truncate rules normally tend to stop the evaluation.
Have a look at that and see if that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-19 12:38 PM
i created the rule again on the decoder and placed it above the other zero payload rule, again calling it botnet beacon.
i then created the rule again in informer, but when i test it i get nothing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-19 12:49 PM
Can you see it in investigator, if you create a custom drill with it? Remember the cache.time.window setting can affect your results. Also for Informer in some cases the results only run from the top of the previous hour backwards so that could be causing your issues.
If you can post screen shots of the rule in Administrator, the custom drill in Investigator and Informer content that might help. Feel free to e-mail me directly if you prefer.
Thank you,
Rui
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-19 12:59 PM
i will send you the screenshots offline in a few minutes.
thanks rui ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-10-25 09:26 PM
As an additional comment on this rule/chart, I'd like to suugest you push the majority of the processing down to the decoder and make the informer/Reporter query much simpler.
First rule:
zero payload
payload='0'
(set to alert to 'risk.info')
Ssecond Rule:
zero payload to threat sources
risk.info='zero payload' && threat.source exists && threat.source!='netwitness' && org.dst exists
(set rule to alert to 'alert')
Informer/Reporter Rule
Select: ip,dst
Where: alert='zero payload to threat sources' && org.dst != '$Good Org Dests'
Create Chart from rule
This puts most of the rule load down on the decoder during capture, and you are only querying the system looking for one primary key value and the list of orgs. If the list of orgs gets too long, make a feed out of it.
- « Previous
- Next »