- NetWitness Community
- Discussions
- How to Detect the Russian Ransom Trojan Beaconing
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Detect the Russian Ransom Trojan Beaconing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-09-16 10:57 AM
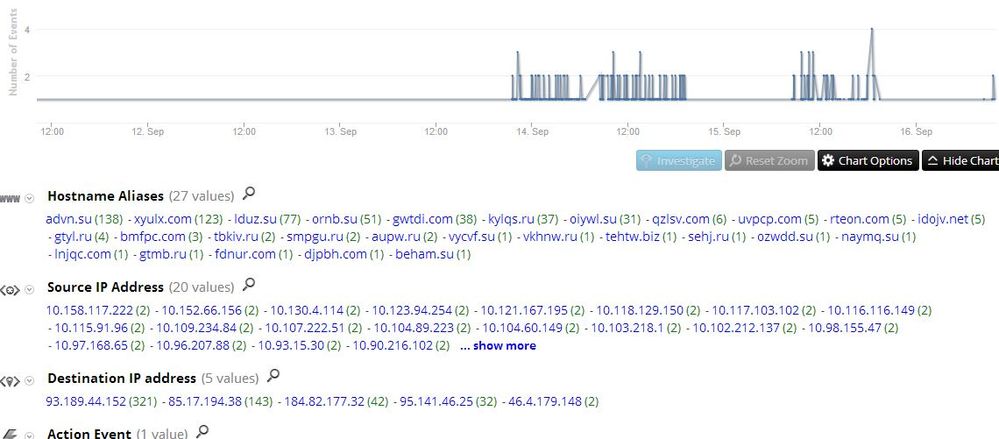
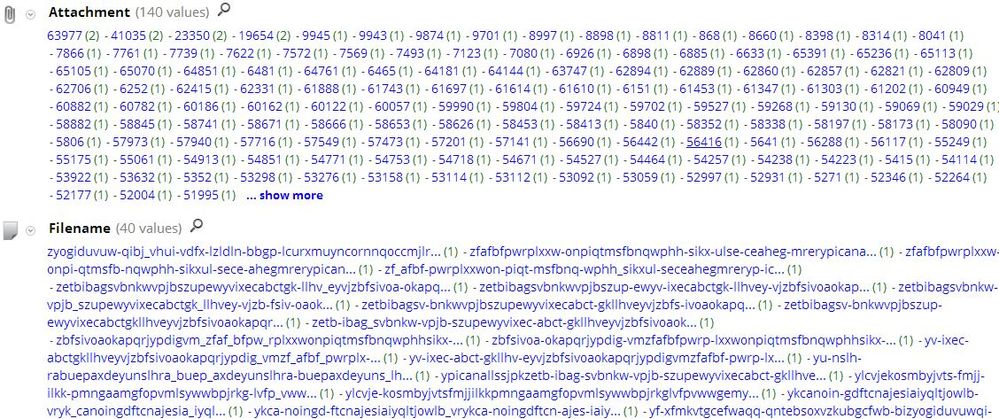
Over the past several days, RSA FirstWatch has detected some unique beaconing from our sandbox to several hosts registered by Russian owners. What makes the beaconing unique is that each HTML checkin page has a unique name, and each session contains a unique attachment. Also, each session is encrypted, so there is really no unique way to detect the traffic based on content. Here is what we saw:
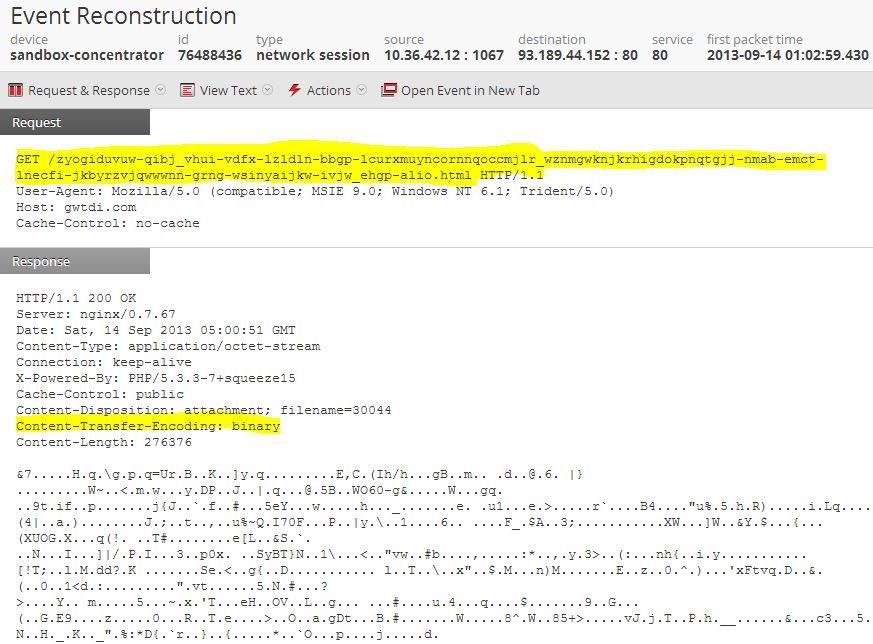
Drilling into a sample reveals this session:
I have highlighted the absurdly long unique .html filename in the get request. Additionally, I have highlighted the binary encoding content transfer type. Finally, each unique session is over 1 MB in size, so whatever this communication is that is taking place is pretty big.
Hosts infected with this ransomware trojan do not do much else on the network. More details on the source infection can be found here at VirusTotal.
You can write a capture rule to detect this activity. My rule to identify this activity looks for the html extension coupled with a filename that is more than 50 characters long. Create a rule and name it Russian RansomWare Trojan Beaconing. The rule content is:
extension=html && attachment exists && filename length 50-u
Give the rule a try as a custom query as well, looking back at the past few weeks in your enterprise. I'd be interested if anyone gets any hits on this.
Happy Hunting!
UPDATE:
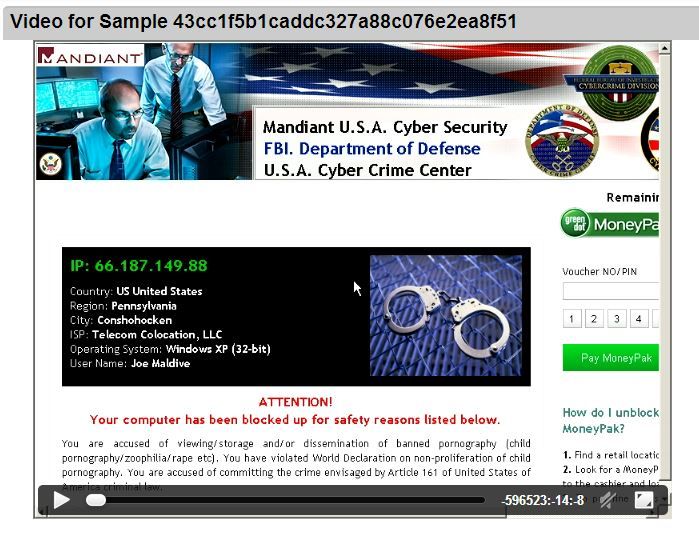
I submitted the original sample to ThreatGrid. When the malware runs, it locks the screen and presents a message from Mandiant and the FBI claiming the system has been blocked for viewing child pornography. Screenshot below.