- NetWitness Community
- Discussions
- Re: How to integrate the RSA Malware Analysis with the Cuckoo Sandbox
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to integrate the RSA Malware Analysis with the Cuckoo Sandbox
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2015-05-22 04:46 PM
Hi everyone!
I updated the post attaching the PPT used during my presentation at the RSA TechFest 2016. Everything that you need to know about the integration process that I developed is avaiable in the file attached.
This is a simple post to show how to integrate the RSA Malware Analysis with the Cuckoo Sandbox solution.
You will need:
- RSA Security Analytics for Packet with Malware Analysis
- Cuckoo Sandbox (local)
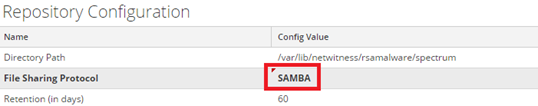
Firstly, you need to enable the File Sharing Protocol on the Service - > Malware Analysis -> Config and then apply the change.
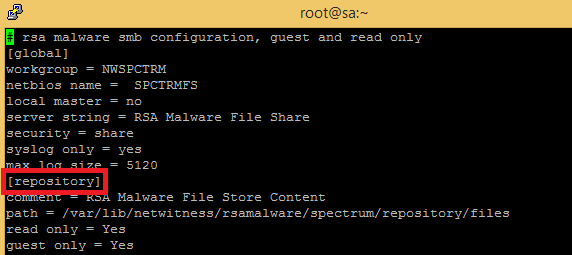
After that, connect through the SSH to your RSA Malware Analysis and change the share name from File Store to repository. Only to remove the space on share name.
Apply the change and restart the smb service.
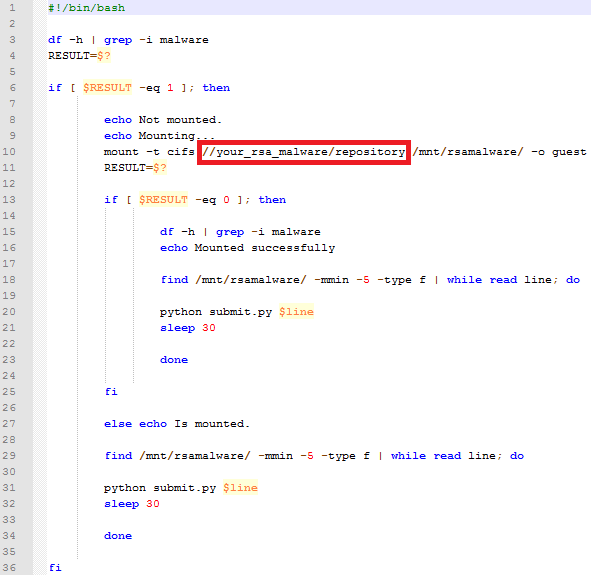
Now, connect through SSH to your Cuckoo Sandbox (local). Run the steps below:
- Install the mount.cifs package
- Make a directory /mnt/rsamalware
- Make a script file rsamalware.sh (image below) on Cuckoo’s utils directory and set as an executable file. Note: Change your_rsa_malware by the correct IP address
Finally, add a cron job to run the script every 5 minutes (in this case). However, you can parameterize the option that better to attendant your specific demand.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-10-17 02:02 PM
Hi Joseph Gumke!
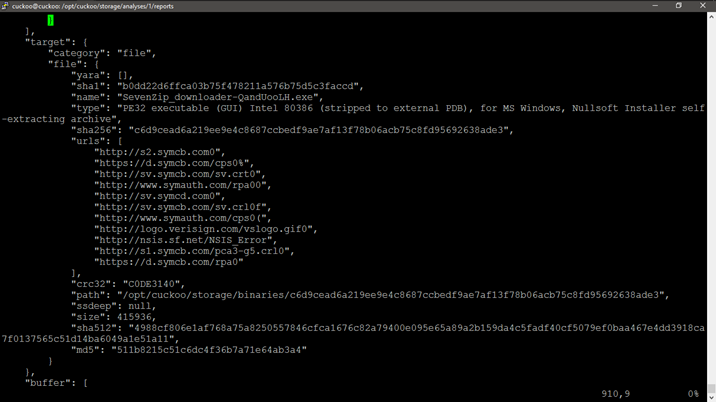
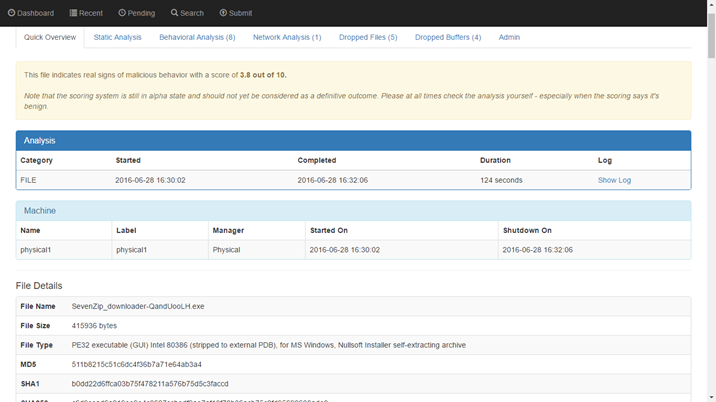
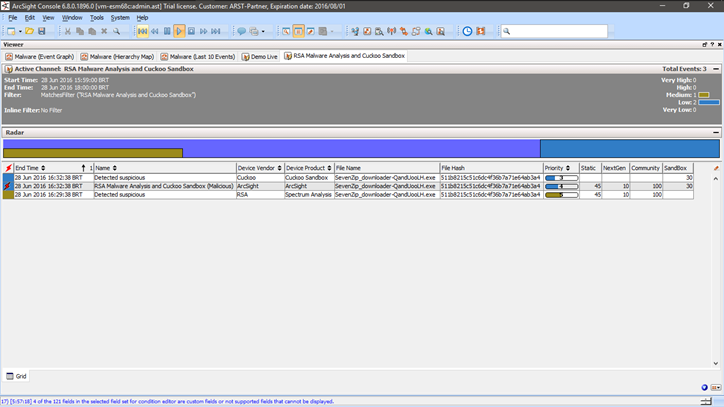
Isn't easier to get the results from the Cuckoo Server? The Cuckoo Server create a JSON file with every info about the analysis process. You can get the file and process them with your SIEM solution. Sometime I did it using the HP ArcSight. Please, see the images below:
1 - JSON file report
2 - Cuckoo report
3 - HP ArcSight
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-10-17 02:09 PM
Hi Ian!
I did it. Now I can see the results from the 4 analysis process into the same screen. Please, see the image below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-10-19 08:33 AM
hard part is that RSA doesnt natively support JSON ingestion, and nobody really knows how to leverage the plugin framework to support this format
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-10-23 11:45 AM
Well, in this case I normally use the Smart Connector from HPE (that is free) to get the events that aren't supported by RSA. After that, I send to the NetWitness through the syslog in CEF format.
- « Previous
-
- 1
- 2
- Next »