- NetWitness Community
- Discussions
- Re: Import This Malicious User-Agent String Feed
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Import This Malicious User-Agent String Feed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-10 02:26 PM
Hello all,
One of the most powerful features of Security Analytics is the ability to create feeds on the fly using the feed creation wizard.
Feeds can be comprised of any values in any meta key. The most common use cases are feeds of malicious IP addresses and Hostname Aliases. However, for this exercise, the RSA FirstWatch Team wants to share its long list of known malware and malicious UserAgent strings. We use this feed internally to identify known malware agents on our own network, and as we discover new malicious User-Agent strings, we will add to this feed as time moves along.
Step 1: Preparation.
In order to take advantage of feeds, you should turn indexing on (IndexValues) for feed.name, feed.category and feed.desc on your concentrators and brokers that will communicate with your capture decoders. This often requires a service restart, so you may need to schedule momentary downtime to get this working properly. The feeds will still work without indexing your values, but any queries against the keys, and any reports that try to take advantage of the new data will be slow to respond to queries.
Step 2. Grab the CSV file.
The CSV file for the feed is attached to the bottom of this post.
Step 3. Run the Wizard.
In Security Analytics, go to Live -> Feeds.
On the next screen, click the big Plus button in the upper right to add a new feed. You will be prompted with a radio button selection. Choose Custom Feed.
Step 4. Program Your Feed
Now you will follow these screen shots to ensure your feed works.
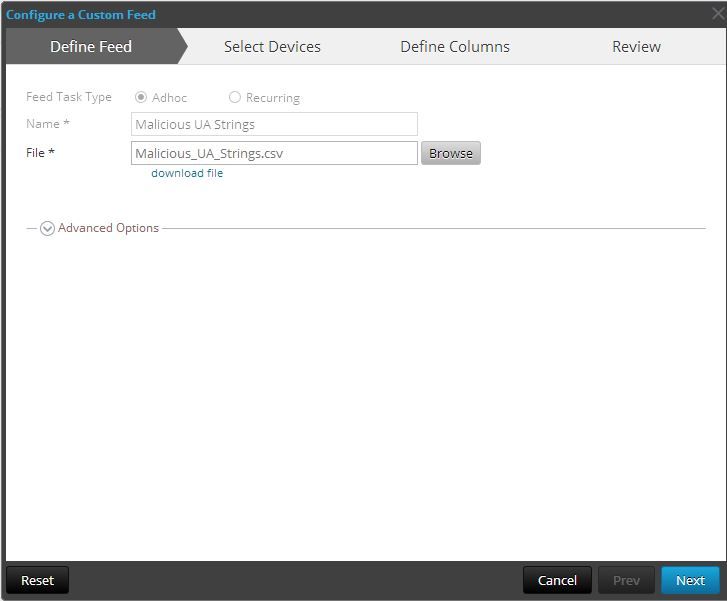
Make sure you are selecting an Adhoc feed. This means it is a one-time installation that can be updated periodically if you need to. Then click Next.
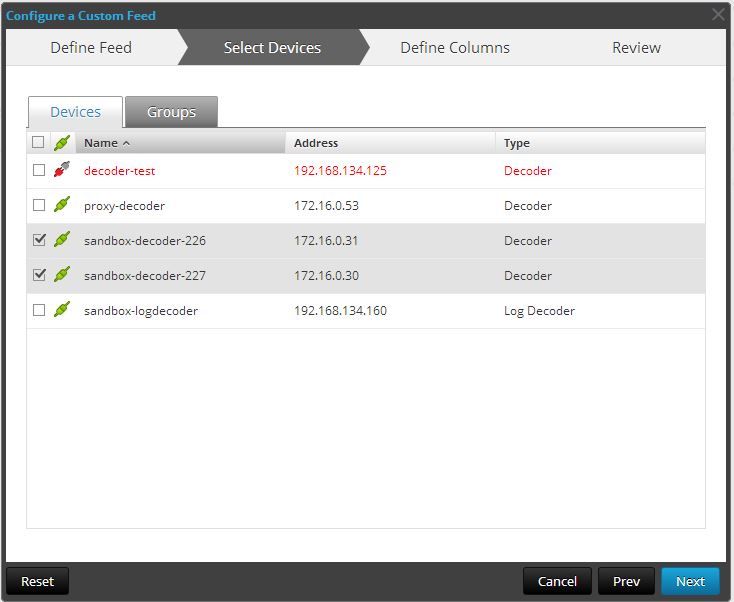
Now you will select which of your decoders are going to house the feed. In my example, my sandbox decoders are selected. Click Next.
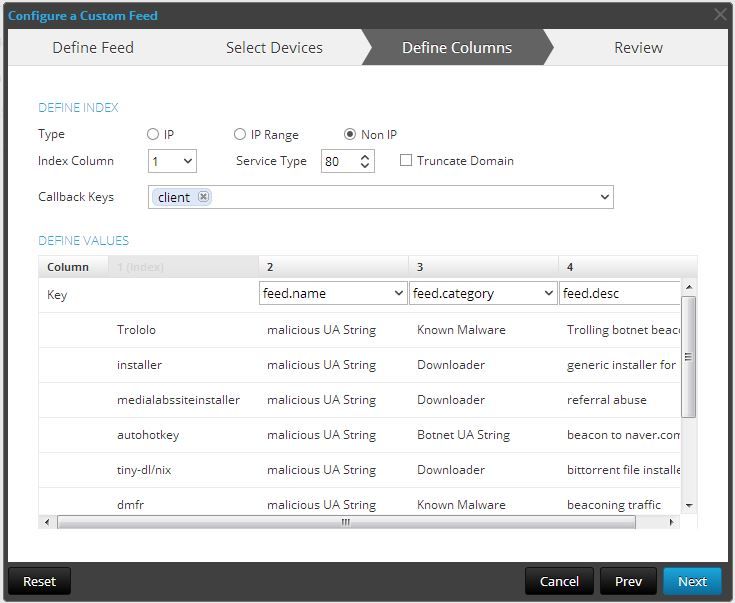
Here is the real configuration screen. Since this is not IP related, choose the Non IP radio button. My CSV is meant to contain all of the malicious user-agent strings in column 1 as my values. So select to index column 1.
Since this is all related to HTTP traffic, I've chosen to select service type 80.
The callback key is the key that is normally populated with the values I want to be on the lookout for. In this case, User-Agent strings populate the client key. So I select the client key for Callback Keys.
When you choose to index column 1, it gets grayed out. Now you need to set the column headers for column 2,3 and 4. In this case, you want to select feed.name as column 2, feed.category as column 3, and feed.desc in column 4.
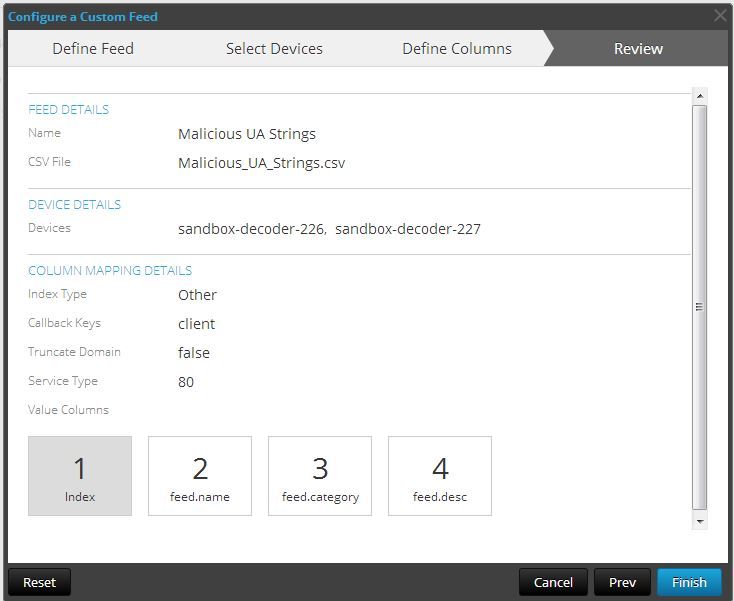
If your screen looks just like below, hit Next.
The next screen is a review screen. Hit Finish and you are done!
Step 5: Look for Results
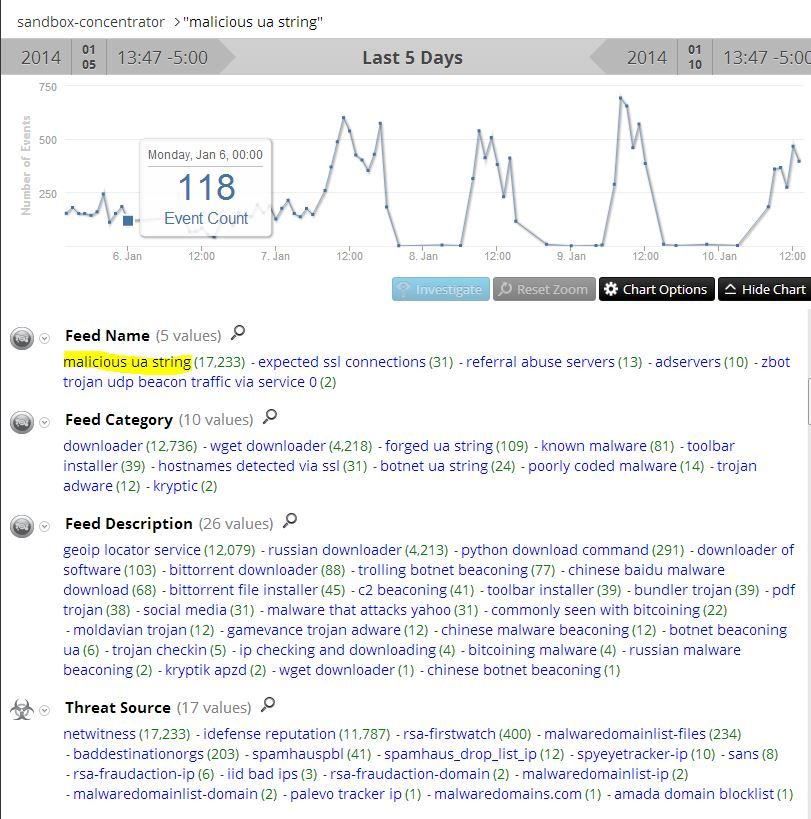
So what does it look like when you get results? Keep in mind that these UA strings are all related to malware communications. Hopefully you won't see too much, but if you do, you may wish to investigate. You could even create daily alerts and reports to monitor for the presence of these know bad UA strings. But in our malware only environment, it looks like this. If you see similar results, you are likely in big trouble.
It should be noted here that we are confident that this simple feed works to identify malicious activity. I simply drilled into the feed name of malicious ua string, and you can read the feed descriptions for the past 5 days. Also note that there are scores of third party feeds that are in agreement that the observed traffic is associated with malware- with iDefense Reputation being the most prevalent, even above FirstWatch. (FirstWatch usually only looks for things that aren't already identified by someone else.)
Step 6: Updating Your Feed:
To update your feed, simply go back to live and feeds, select your feed and click the edit button.Under step 4 above, you will see a link to download your feed. It will download as a CSV file for easy local editing. And if you want to change the categories and descriptions we've put in place, feel free to do so. When you finish editing your feed, use the wizard to upload it again. You will not have to change any of the configuration parameters.
Good luck and happy hunting!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-13 03:36 PM
I forgot to mention that your UA strings that you add to this feed is CASE SENSITIVE. So when you add new UA strings, copy and paste from the session view, not the meta view in Investigator, which forces everything lowercase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-14 11:08 AM
Hi,
I am trying to get this feed working for a 9.8 environment, and I am new to creating feeds. Below is what I believe the XML should be:
<?xml version="1.0" encoding="utf-8"?>
<FDF xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:noNamespaceSchemaLocation="C:\Users\nelsoj12\Documents\scripts\feed-definitions.xsd">
<FlatFileFeed name="Malicious UserAgents"
path="useragents.csv"
separator=","
comment="#">
<LanguageKeys>
<LanguageKey name="feed.name"
valuetype="Text"/>
<LanguageKey name="feed.category"
valuetype="Text"/>
<LanguageKey name="feed.desc"
valuetype="Text"/>
</LanguageKeys>
<Fields>
<Field index="1" type="index"/>
<Field index="2" type="value" key="feed.name"/>
<Field index="3" type="value" key="feed.category"/>
<Field index="4" type="value" key="feed.desc"/>
</Fields>
</FlatFileFeed>
</FDF>
When I try to compile it with NwConsole I get:
NetWitness Console 9.8.5.15
Copyright 2001-2012, NetWitness Corporation. All Rights Reserved.
> feed create UserAgent.xml
Creating feed Malicious UserAgents...
done. 0 entries, 167 invalid records
All feeds complete.
Any help would be greatly appreciated.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-15 10:08 AM
Looks like you are missing a meta callback to the client key.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-16 12:35 PM
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-16 12:39 PM
Hey, if you get it to work, please post a working XML flatfeed file here for users still on 9.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-16 12:47 PM
Will do. As I said, I am new to creating manual custom feeds and not quite sure how to implement the meta callback. What I am thinking of doing is creating the feed via 10.3 and trying it in 9.8. The feeds from Live work in 9.8 so this should work too... I think.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-02-05 11:21 AM
I have updated this feed since it was first posted. It now has several UA strings that seem to be common to DDoS malware on your network. This specific DDoS malware make hundreds of get requests to a webserver in the '/" directory using one of these forged UA strings. There are also dynamically generated referer strings as well, so if you get hits on the DDoS portion of the feed, you can validate it by looking for these characteristics.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-06-16 05:25 PM
Jon,
I was wondering if you were able to get this working in 9.8. If you did get it working in 9.8 could you please provide me with the working xls.