- NetWitness Community
- Discussions
- Is Your Service Type OTHER Hiding Zbot Beaconing?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Is Your Service Type OTHER Hiding Zbot Beaconing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-21 01:37 PM
The latest variants of Zeus or Zbot aren't as easy to detect like they used to be. They used to checkin to their Command and Control servers using specific filenames like "in.php" followed by a digital string. The webserver would then issue an 200 OK message, issue its next command, and the whole thing would repeat like clockwork every few minutes.
Now most variants are UDP based. They don't rely on replies from the webserver and the payload is typically encoded. Worse yet, there is no clear pattern of beaconing. This makes signatures obsolete as a detection. You also can't rely on network statistics to catch it either.
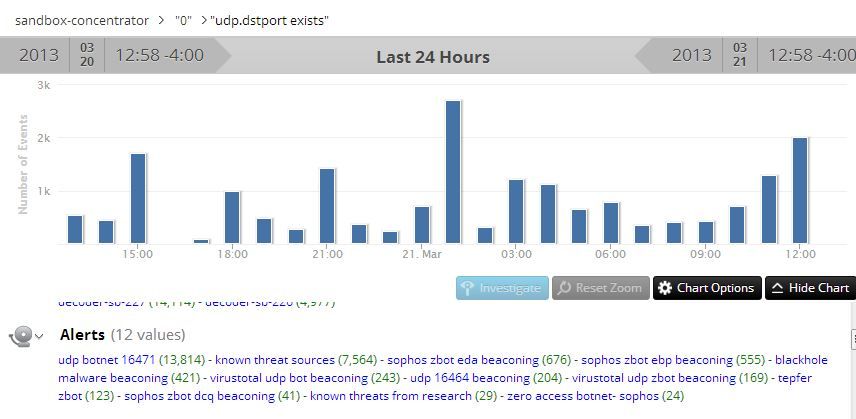
In RSA FirstWatch, we are running constant streams of malware and infected VMs past some heavy-duty decoders to find the latest threats, patterns and trends. Below are some recent rules that everyone should preview to find some of these latest threats. And check out the massive UDP Botnet traffic we are already identifying!
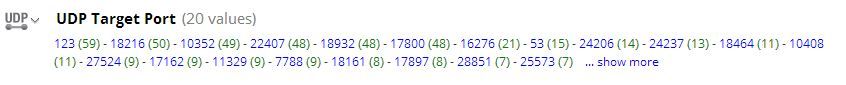
But to find UDP beaconing on your own, look in service OTHER, click on the UDP Target Port EXISTS drill and start looking at unusual highport UDP traffic. The trick here is to locate new botnets you don't already know about, so I'll filter out all of my alerts shown above. Now I am left with a list of UDP High Ports that should be looked at and researched to see if the IPs involved match any known published ZBot variants.
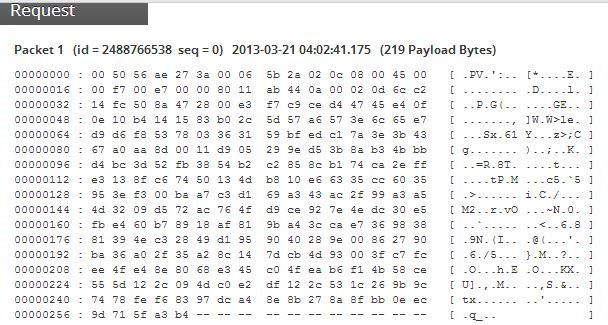
Drilling into the highest value port, 18216, shows multiple VMs all visited the same destination IP. I'm going to guess its malicious, but want to drill into the session to inspect the traffic.
And yes, the payload looks encoded.
So now I Google search the destination IP and I come up with a Sophos Page that describes the exact traffic I'm seeing to this host, released two days ago, which is called Troj/PWS-CBX. This page also helpfully lists a number of additional IP addresses and ports I can use to create a new Detection Rule. I would call this rule Sophos UDP Beaconing Troj/PWS-CBX
its contents: service=0 && ip.dst=106.204.182.27,108.194.20.252,110.171.74.52,124.253.27.135,184.90.193.177,194.94.127.98,217.92.79.126,37.220.112.38,68.255.44.96,76.120.184.148
Now I have taken a new piece of observed malware behavior, automated its detection, and will be able to identify it going forward. Tomorrow I'll filter out that activity as well so I can concentrate on finding only new threats.
So keep your eyes on that unusual high-port UDP traffic. Its likely hiding Zbot variants.