- NetWitness Community
- Discussions
- Looking for Double File Extensions in Mail Attachments
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Looking for Double File Extensions in Mail Attachments
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-01-27 06:35 PM
I am looking for the syntax to use a REGEX statement in an ESA rule that calls a list (extensions) from the Contexthub. In this particular rule, device.type = ciscoiportesa. File attachments are listed in the meta Filename. From one of our Content Engineers, I was able to get his regex that he is using in a different SIEM platform.
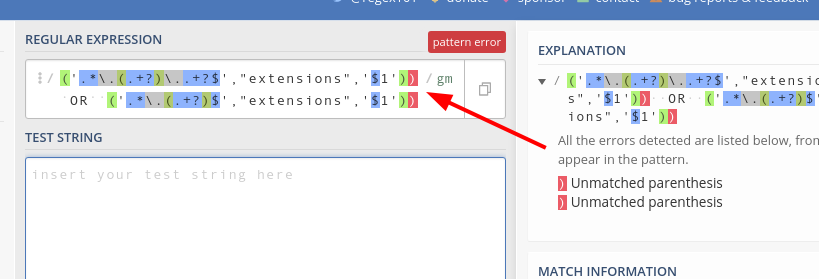
RegEx used: ('.*\.(.+?)\..+?$',"extensions",'$1')) OR ('.*\.(.+?)$',"extensions",'$1'))
What I have built so far:
SELECT * FROM Event(
/* Statement: Extensions */
(filename IS NOT NULL AND EXISTS (SELECT * FROM extensions WHERE ( LIST = Event.filename ) ))
AND
/* Statement: Device Types */
(device_type IN ( 'ciscoiportesa' ))
AND
/* Call REGEX */
(filename REGEXP '.*\.(.+?)\..+?$',"extensions",'$1') OR ('.*\.(.+?)$',"extensions",'$1'));
I am getting an error when I try to save my rule (not wholly unexpected): Syntax error in module. Incorrect syntax near ',' expecting a closing parenthesis ')' but found a comma ',' at line 12 column 38. As far as I can tell it is not happy with my regex.
Thanks for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-01-28 01:00 PM
Can you explain exactly what your use case is here? What are the contents of the extensions LIST, and why do you need to use regex to match against it?
Also, it appears your regex has two extra right parenthesis:
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-01-29 07:27 PM
Hi Josh,
Thank you for responding. The purpose of this rule is to trigger when an attachment name contains at least two consecutive file extensions (for example virus.exe.txt, presentation.bat.pptx) and where one of them is associated to an executable file (such as exe or bat). I am not sure how to call up the comparison file (extensions) within ESA and have the regex utilize it. The regex works in one of the other SIEM's that we support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-02-01 05:41 PM
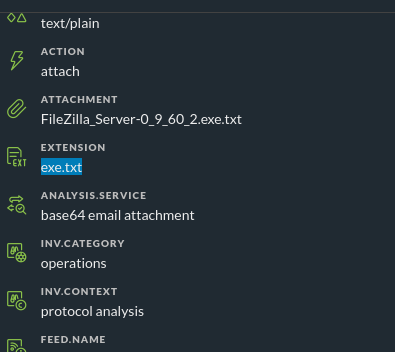
I don't know that using a context hub list will be appropriate for your use case. In some traffic from my lab for files with multiple extensions, the extension meta key ended up like this:
Your traffic may be different, but if not then you'd need to have every single one of these possible multiple-extension strings defined in your list (because we can only do exact string matching with context hub lists currently)....which is not exactly a reasonable or feasible task...
That said, when it comes to doing the actual matching of your filenames, you'll have a few different options (https://community.rsa.com/docs/DOC-104243#Multi-Va😞
- REGEXP (as you tried already)
- matchLike
- matchRegex
- asStringArray
Some examples of what these could look like for your use case:
@RSAAlert
@Name('REGEXP alert')
SELECT * FROM Event(
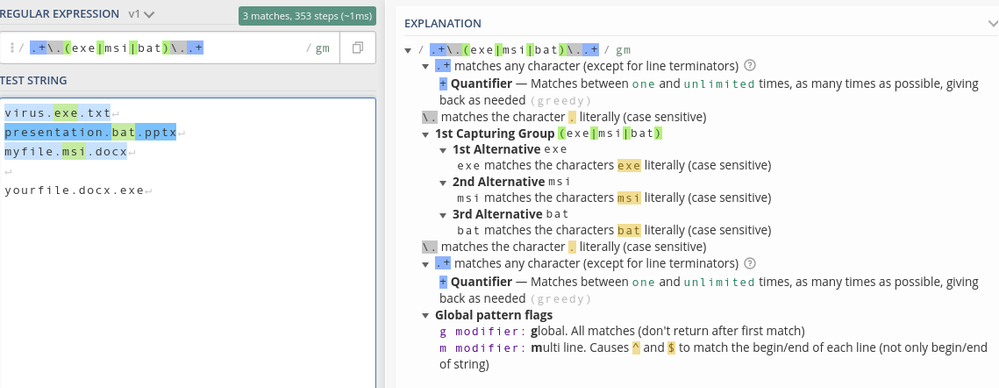
(asStringArray(filename)).anyOf(v => v REGEXP '.+\.(exe|msi|bat)\..+')
);
@RSAAlert
@Name('matchLike alert')
SELECT * FROM Event(
matchLike(filename, '%.exe.%')
OR matchLike(filename, '%.msi.%')
OR matchLike(filename, '%.bat.%')
);
@RSAAlert
@Name('matchRegex alert')
SELECT * FROM Event(
matchRegex(filename, '.+\.(exe|msi|bat)\..+')
);
These will explicitly look for exe, msi, and bat extensions (of course, you can add more), but this is a bit rigid.
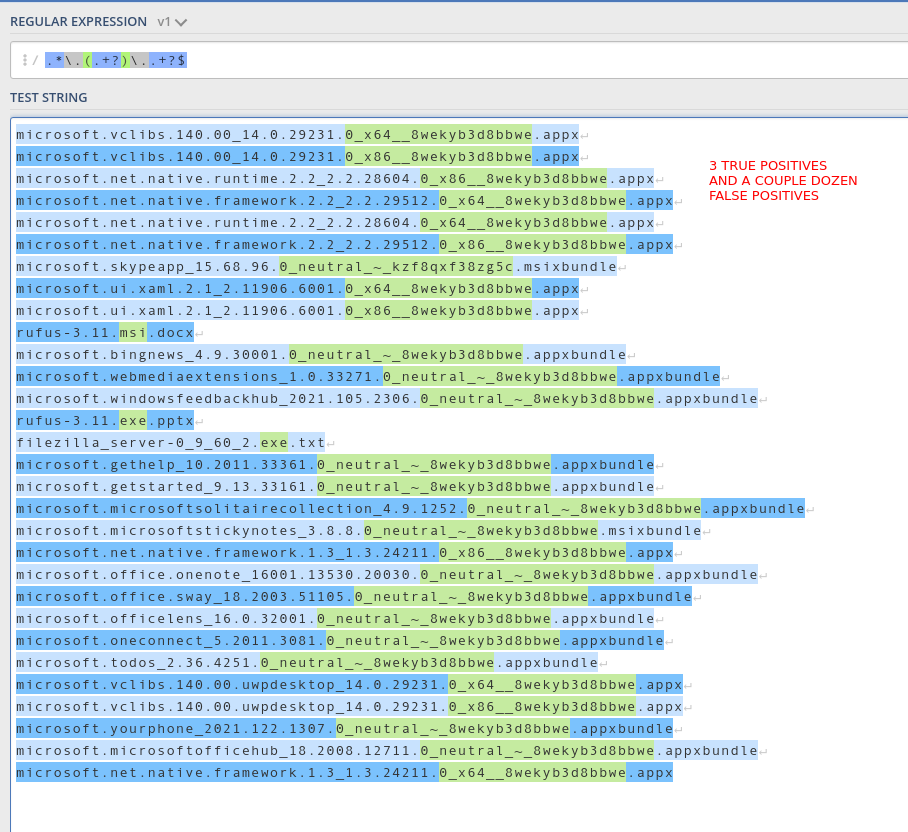
If you want to just match against any/all files with a filename.ext1.ext2 type of structure, you could replace the regex above with your original regex....but that will generate a whooooooole lot of false positives so I'd recommend you add some additional filtering to your rule to try to eliminate those as much as possible.
Mr. Mongo