- NetWitness Community
- Discussions
- Re: Looking for searching criteria on SA based on Filename
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-22 03:50 AM
Dear Friends,
I want to search a infection based on file name and the filename information provided below
Find the below info which shows a successful exploit callback. I am not sure how to make search on SA with file name since the file name is alphanumeric and its gets change randomly. I believe there could be lots of infection with same pattern. We use only packet decoder so regex won't work.
Please note that i want search with only filename since the directory field is always empty.
 | orig_ip : | 10.32.7.154 |
 | ip.addr : | 10.32.7.154 |
 | action : | post |
 | alias.ip : | 188.165.235.115 |
 | directory : | / |
 | filename : | 6197C9EB5912A0CF20F5E130E79F0B14 |
 | content : | application/x-www-form-urlencoded |
 | client : | Mozilla/5.0 (Windows NT 6.1; WOW64; rv:26.0) Gecko/20100101 Firefox/26.0 |
 | alias.ip : | 188.165.235.115 |
 | alert.id : | nw32550 |
 | risk.info : | http direct to ip request |
 | threat.category : | spectrum |
 | threat.source : | netwitness |
 | orig_ip : | 10.32.7.154 |
 |
Thank you,
Awaiting for valuable response.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-22 04:44 PM
Looks like the same exploit activity as here on UrlQuery.
urlquery.net - Free url scanner
To get this rule to work, look for" action=put && directory='/' && filename length 32 "
I'd be curious to know what this type of malware is if you are willing to share?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-22 02:01 PM
I would try to search for : action = post && alert.id = nw32550 and look up for all file names
you should not get to many...
to detect this kind of callback, maybe a lua parser that look at file name length, with a specific size if the name change randomly, but not the number of characters...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-22 04:44 PM
Looks like the same exploit activity as here on UrlQuery.
urlquery.net - Free url scanner
To get this rule to work, look for" action=put && directory='/' && filename length 32 "
I'd be curious to know what this type of malware is if you are willing to share?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-23 03:29 AM
Dear Fielder,
Thank you so much for your response and the correct answer. Today is holiday here i couldn't get chance to search with the rule which you have provided.
Please find the details of the malware below:
This has been identified as RIG Exploit Pack as reported by Kahu Security: http://www.kahusecurity.com/2014/rig-exploit-pack/
Asprox-style callback malware:
04:10:02 - 46.237.71.11 - xxxx.com - GET /componentsjumla-q1/jquery/ [Repeats]
04:09:55 - 46.160.112.212 - xxxx.com - GET /b/shoe/1928 [Repeats]
04:10:50 - 46.237.71.11 - xxxxx.com - GET /jshoppresto-d2/soft32.dll
Post-infection callback for W32/Asprox. (Kuloz -IDS SNORT ) Bot POST CnC events and Trojan-Spy.Win32.Zbot.hmcm Checkin:
Snort detected this type of infection as Kuloz callback.
04:11:17 - 46.98.158.160 - xxxxx.com - GET /b/eve/a0e7a0e4c280b78aaf7ec6fd
04:12:12 - 62.16.38.131 - 188.165.235.115 - POST /b/opt/3ACC6DEAE44C9D2F862B8A41
04:12:13 - 62.16.38.131 - xxx.com - GET /b/letr/7D76278E4C0344012E64536F
04:12:14 - 62.16.38.131 - 188.165.235.115 - POST /b/opt/4F3F27C669A8A5480BCFB226
04:12:31 - 62.16.38.131 - 188.165.235.115 - POST /b/req/0B87F5A8C3E5E730A182F05E
04:12:51 - 62.16.38.131 - 188.165.235.115 - POST /b/req/8C1289B1DB772C6AB9103B04
04:12:51 - 62.16.38.131 - 188.165.235.115 - POST 188.165.235.115:8080 /6197C9EB5912A0CF20F5E130E79F0B14
04:12:51 - 62.16.38.131 - 188.165.235.115 - POST 188.165.235.115:8080/6197C9EB5912A0CF20F5E130E79F0B14
I hope this will help for better understanding....!
Please do let me know if you would like any other info.
Thanks,
Tulsi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-23 09:02 AM
Tulsipriyan,
The beacon pattern you describe sounds very much like Kargen which I blogged about here.
The Kargen Zbot and How to Detect It
RIG can be used to force hosts to join any type of botnet. I saw one version yesterday where filename=proxy.php && query begins 'req'
Also, that 32 char string is base 64 decoded commands.
Also, that user-agent string is a known forged UA and we see that specific Jan 1 2010 firefox version associated with all types of malware and DDOS traffic. I think I had even added it to my known list of malicious UA strings (another blog post)
So do a deep search for that UA string on your enterprise. If you find it, its a sign of something bad.
Thanks for sharing!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-23 11:00 AM
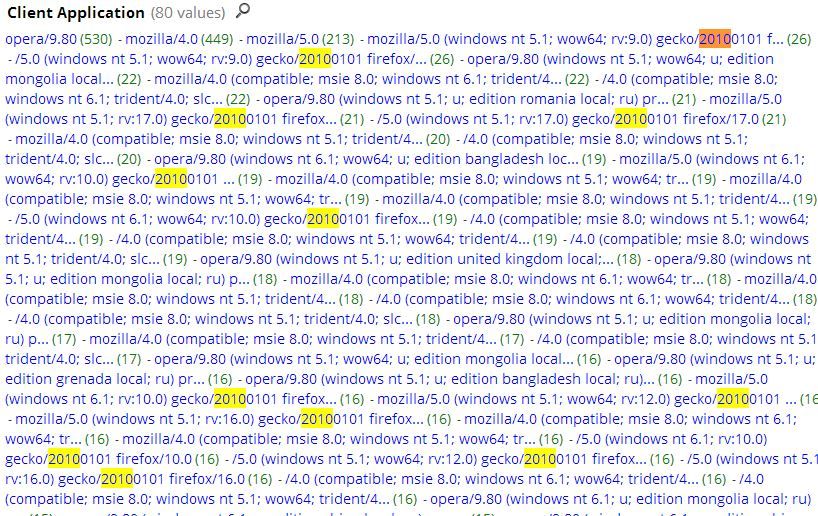
As an example of what I mean about the UA string with the 20100101 date stamp, look at this screen shot taken from today by malware that launches DDoS attacks against a website using thousands of forged UA strings. See the pattern? So any browser with a date stamp of jan 1 2010 should be held in suspicion. Malware authors constantly reuse code for all kinds of things and this date stamp seems to be a recurrent piece of code.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-25 02:10 AM
Hi Fielder,
I couldn't get chance to look at your blog previously. Now i saw that and looks like the same beacon pattern which i have described.
The first malware callback appears to be same "
action=put && directory='/b/req/', '/b/opt/'
Thanks for your valuable answers.
Regards,
Tulsipriyan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-25 02:40 AM
Hi Fielder,
I have a query regarding SA sessions contains multiple users packets.
We are capturing packets between proxy and websense by placing decoders. And when we are searching any traffic for particular user or domain SA shows many users traffic as result. The problem occurs becuase each sessions contains multiple user packets. Since source is same for all users as proxy. We have reached to support and they said by creating some custom parser that can splitted. Do you have any idea ?
If you have any idea please reach ome through thulasi.deivasigamani@emc.com
Thanks,
Tulsipriyan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-28 02:49 PM
re: "We use only packet decoder so regex won't work."
Excuse me? Really? This query works fine in both the fat client Investigator and the Gui Investigate.
service=80 && action=put && tcp.dstport=8080 && directory=/ && filename regex '([A-Fa-f0-9]){32,}'
Unforturnately, it fails "validate" in the App Rule dialog.
Don
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-05-30 01:02 AM
RE: Unforturnately, it fails "validate" in the App Rule dialog.
stick some single quotes around the text values and your rule will pass the validation check for app rules:
service=80 && action='put' && tcp.dstport=8080 && directory='/' && filename regex '([A-Fa-f0-9]){32,}'
works for me.