- NetWitness Community
- Discussions
- NWE Windows DNS Analytics Logs
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NWE Windows DNS Analytics Logs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-24 12:29 AM
Hi All,
With the ability of NWE being able to ship Windows Event Log sources to NetWitness, does that mean it's possible to ship the DNS Analytics logs into NetWitness instead of the old DNS Debug text file logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-24 10:51 AM
HI Jeremy,
NetWitness Endpoint is designed to be able to collect logs from any Windows Event channel. Let me look into the parsing aspect and get back to you.
Thanks,
Guy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-24 04:53 PM
I looked into this about 2 months ago with some assistance from David Glover and Con O'Donnell and could not get either winRM or the endpoint agent to successfully collect the DNS/Analytical logs.
There are a couple anomalies with these logs:
- the channel name shown in Event Viewer vs. the channel name shown in any of the logs details
- the actual filetype compared to several other event logs that we collect from without any issues
I could not figure out a solution to collect these logs, and for that matter, adding either channel name above to either of my windows collection methods (winrm and endpoint agent) completely broke both, and no windows collection would occur until I removed the DNS channel.
If anyone is able to get this working through either winrm or the endpoint agent, that would be an enormous improvement for DNS logging over the current "audit log written to a flat file" method.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-24 09:54 PM
Thanks for sharing your experience. I really hope there is a solution to this, I'd rather not have to install another agent onto the DCs in order to collect DNS query logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-24 09:54 PM
Thanks Guy,
I look forward to hearing what you find out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-25 03:55 PM
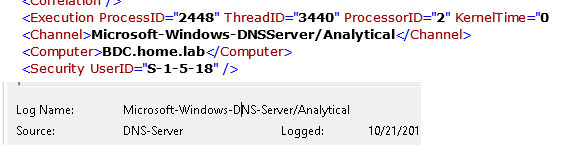
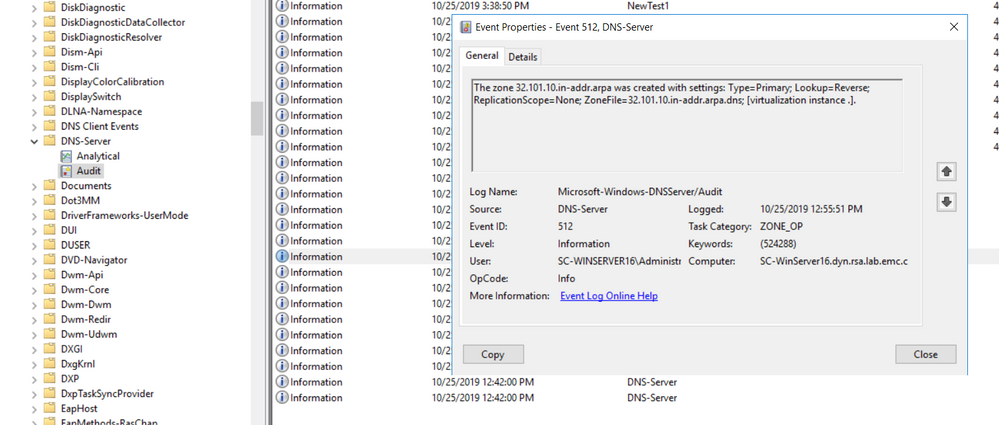
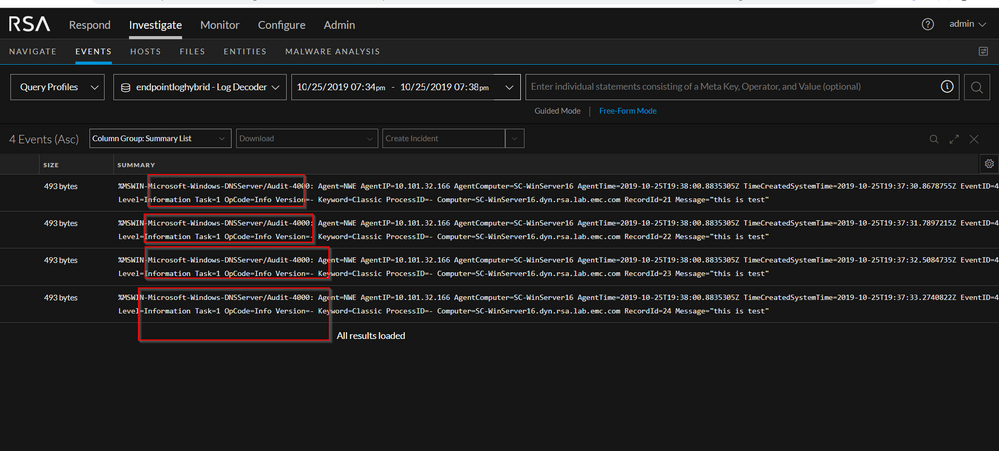
I tried to setup DNS server and was able to generate some traffic under Microsoft-Windows-DNS Server/Audit as below and was able to successfully recieved it using Netwitness UI. Key is to add right channel. In this case Channel i added was Microsoft-Windows-DNSServer/Audit. Unfortunately I did not had any logs under Analytical directory but I see no difference when Endpoint Agent tries to collect it. Also I noticed in one of the above screenshot, file generated for analytical log is .etl, On windows 2016 atleast, i see that it recommends to save all events when you are enable analytic log from Event Viewer and default format is .evtx which is same as any other log(something to be careful about when saving events). Will be happy to take a look at problematic setup if possible
AS can be seen, under investigate:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-10-25 05:13 PM
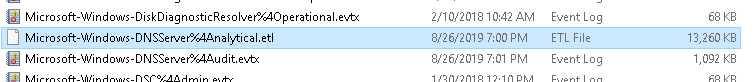
These Analytical logs are not saved in EVTX format, they are saved in ETL format:
I tried changing the filetype from ETL to EVTX manually when i tried this initially, with no change in outcome.
If you are aware of a way to change how the DNS/Analytical logs are saved so they write to an EVTX file instead of ETL, then that would likley enable collection.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-11-24 09:51 PM
Hello
Is the problem with reading the ETL file (%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-DNSServer%4Analytical.etl) due to the issue described in the following online articles?
https://support.microsoft.com/en-ca/help/2488055/error-when-enabling-analytic-or-debug-event-log
QRadar WinCollect: Collecting DNS Server Analytic Logs
These articles mention,
For analytic and debug logs, Event Viewer does not allow events to be queried or viewed if the log is both enabled and has Overwrite events as needed (oldest events first) configured.
The work-around is for Analytic and debug logs is to use the default setting, Do not overwrite events (Clear logs manually).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-05-10 12:11 AM
Testing in my Lab, I found can collect logs from the channel: Microsoft-Windows-DNSServer/Analytical by disabling logging on the Windows Server in the Event Viewer for this channel.
Only then NetWitness can collect the channel: Microsoft-Windows-DNSServer/Analytical logs.
However re-enabling the channel: Microsoft-Windows-DNSServer/Analytical the old logs are all deleted from the Windows server, and the EventRecordID starts again from 0 for new logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-10-14 05:30 AM
Hi
Can you please explain the complete steps which I need to do for collecting the DNS logs in RSA Netwitness (V 11.4.0.0) which were save at client end at location C:\analytic_audit.etl.