- NetWitness Community
- Discussions
- Re: Supress ESA alert/incident for a known good file 'Outbound from Unsigned AppData Directory'
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-07-09 02:55 AM - edited 2021-07-09 02:56 AM
We have an internal app used for Instant Messaging that uses an Electron based front end in the local users AppData directory.
It generates a lot of alerts in the Respond module for module 'Outbound from Unsigned AppData Directory'.
What's the best way to supress or allow list this alert so I'm not getting all the noise.
| Timestamp | 09/07/2021 04:47:17.000 pm 2 minutes ago | ||||||||
| Type | Endpoint | ||||||||
| Source |
|
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-07-09 11:19 AM - edited 2021-07-09 11:24 AM
@Anonymous
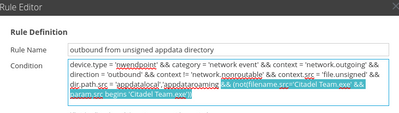
The best option for both this and your Runs Malicious File By Reputation Service question will be to adjust the app rule on the log decoder that is source of the alert.
In the log decoder config menu find the "outbound from unsigned appdata directory" rule and add the meta for your known-good apps/processes to these. Using your Citadel Team details as an example, you could add:
&& (not(filename.src='Citadel Team.exe' && param.src begins 'Citadel Team.exe'))
Note that I am purposefully excluding the sha256 value here, as that will change after any upgrade to citadel team, as well as leaving out much of the launch arguments because I don't know whether those will remain consistent.
I am also not including the source directory, but I believe there is some explicit appdata meta that gets created in these events....in context.src possibly? I cannot find this in my lab at the moment, but I expect you'll have some good examples to draw from.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2021-07-09 11:19 AM - edited 2021-07-09 11:24 AM
@Anonymous
The best option for both this and your Runs Malicious File By Reputation Service question will be to adjust the app rule on the log decoder that is source of the alert.
In the log decoder config menu find the "outbound from unsigned appdata directory" rule and add the meta for your known-good apps/processes to these. Using your Citadel Team details as an example, you could add:
&& (not(filename.src='Citadel Team.exe' && param.src begins 'Citadel Team.exe'))
Note that I am purposefully excluding the sha256 value here, as that will change after any upgrade to citadel team, as well as leaving out much of the launch arguments because I don't know whether those will remain consistent.
I am also not including the source directory, but I believe there is some explicit appdata meta that gets created in these events....in context.src possibly? I cannot find this in my lab at the moment, but I expect you'll have some good examples to draw from.
Mr. Mongo