- NetWitness Community
- Discussions
- Re: TEST RULE WITH TIME INTERVAL
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
TEST RULE WITH TIME INTERVAL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-03-18 11:36 AM
Hi,
I would like to test a rule with time interval. How can i do it?
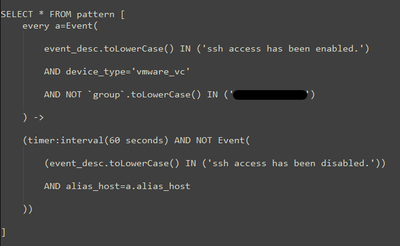
I have the following condition:
device type, event description, time interval e group.
The rule is the following:
- Labels:
-
RSA NetWitness Platform
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-09 07:22 PM
Dear Riccardo,
To my understanding there exists a limitation within the Netwitness ESA Test Rule section pertaining to the integration of Interval (timer:interval).
It is imperative to note that currently, there is no available method to test the time interval via the Test Rule section. However, it is feasible to evaluate the ESA rule logic by excluding the timer(interval) from the ESA rule and inputting all event meta instead.
It is crucial to emphasize that while the testing of timer:interval is unavailable, the comprehensive logic of the rule can still be thoroughly assessed.
I hope this answers.
Thanks
Allen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-10 08:28 AM
Dear Allen,
Thanks for your support and information.
I would like to know if there's a workaround to this method.
I read that someone suggest to use a tool to ingest test logs directly to the decoder. Is this information correct? And in case, could you tell me the name of this tool and suggest me steps to do this test ?
Regards,
Riccardo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-10 11:11 AM
Dear Riccardo,
I trust this message finds you well.
In relation to testing an ESA rule online, I would recommend the following steps.
1. Configure ESA deployment and data source for testing purpose.
2. Deploy the rule into ESA deployment.
Additionally, to inject log events in syslog format, you can utilize the NwLogPlayer tool located at logdecoder /usr/bin/NwLogPlayer.
(Please contact NW Support if there is no NwLogPlayer installed on Logdecoder).
For further details about NwLogPlayer, please refer to the following link: https://community.netwitness.com/t5/rsa-netwitness-platform-presales/rsa-security-analytics-demo-log-traffic-simulation-with/ta-p/570166.
Regards,
Allen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-11 06:49 AM
Dear Allen,
thank you for explanation but when i tryed to open link i recived ACCESS DENIED.
Regards,
Riccardo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2024-04-11 11:09 AM
Dear Riccardo,
I copied the article content here for your reference.
RSA Security Analytics Demo Log Traffic Simulation with NwLogPlayer
Log Traffic Simulation
Loading ad hoc log files may be done through the RSA Security Analytics interface or by running a utility such as NwLogPlayer.
See this article for more information on uploading to a log decoder - https://community.rsa.com/docs/DOC-54879
See this article for more information on NwLogPlayer - https://community.rsa.com/community/products/netwitness/blog/2016/10/10/how-to-replay-logs
Log File Types Accepted by NwLogPlayer
Log files may consist of one of several different formats.
.dev
An entry in a .dev file consists of the syslog priority + raw syslog
Format:
<priority><raw syslog information>
Example:
<134> %PIX-6-302016: Teardown UDP connection 22588139 for outside:82.162.129.243/53 to dmz:10.10.100.16/1024 duration 0:00:01 bytes 169
.unx
A .unx file is output from the enVision lsdata command. It has the date/time and device ip address prepended to the raw log data. NwLogPlayer ignores the datetime and [device ip addr].
Format:
datetime [device ip addr] %<identifier> <raw syslog>
Example:
Apr 23 09:00:17 [143.5.113.2] %PIX-6-302016: Teardown UDP connection 22588139 for outside:82.162.129.243/53 to dmz:10.10.100.16/1024 duration 0:00:01 bytes 169
.log
Syslog outputs four fields:
- The human-readable timestamp for the message
- The originating machine
- The name and PID (if applicable) of the originating process
- The text of the message
Format:
<timestamp> <originating machine> <name and PID of originating process> <raw message>
Example:
Oct 17 08:59:24 peradam.cs.colorado.edu sendmail[21601]: e9HExOW21601: SYSERR(root): Can't create transcript file ./xfe9HExOW21601: Permission denied
NwLogPlayer
NwLogPlayer is a command line utility located on demo VMs in /usr/bin. It is a utility that works similarly to tcpreplay to simulate syslog traffic. It has several arguments, listed in the table below. It can process several file types.
Usage Example:
NwLogPlayer -s 192.168.254.115 –r 3 –f vmware.log
-s 192.168.254.115 IP address of the log decoder
-r 3 automatic detection of raw mode
-f vmware.log Log file to upload
--priority arg |
set log priority value |
-h [ --help ] |
show this message |
-f [ --file ] arg (=stdin) |
input file |
-d [ --dir ] arg |
input directory |
-s [ --server ] arg (=localhost) |
remote server |
-p [ --port ] arg (=514) |
remote port |
-r [ --raw ] arg (=0) |
Determines raw mode. 1= File contents will be copied line by line to the server. 0 = add priority mark 3 = auto detect 4 = envision stream 5 = binary object -r 3 expects syslog priority as the first part of the entry. It will prepend a syslog priority to the entry if one is not found |
-m [ --memory ] arg |
Speed test mode. Reads up to MB of messages from the file contents |
--rate arg |
Number of events per second. No effect if rate > eps which program |
--maxcnt arg |
max number of messages to be sent |
-c [ --multiconn ] |
multiple connection |
-t [ --time ] arg |
simulate time stamp time. Format as yyyy-m-d-hh:mm:ss |
-v [ --verbose ] |
if true will verbose output |
--ip arg |
simulate ip tag. |
--ssl |
connect with SSL |
--certdir arg |
OpenSSL certificate authority directory. |
--clientcert arg |
use this PEM-encoded SSL client certificate |
--clientkey arg |
use this PEM-encoded private key file. If not specified, the clientcert path is |
|
--udp |
send in udp
|
I hope this helps.
Regards
Allen