- NetWitness Community
- Discussions
- Re: updating Public CA certificate on 11.1
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-23 07:33 AM
Hi All,
Is there any article how to update the Public ca certificate and server certificate for NW server console. I am not able to find any article for 11.1
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-23 09:37 AM
This is taken from the security config guide. I can confirm that this works perfectly.
1.Rename your certificate files and save them in for NGINX.
Rename the customer provided cert.pem certificate pem file to web-server-cert.pem.
Rename the customer provided key.pem key pem file to web-server-key.pem.
Rename customer provided cert.chain certificate chain file to web-server-cert.chain.
Rename cert.p7b certificate p7b file to web-server-cert.p7b.
2.SSH to the NW Server.
3.Replace the existing NetWitness Suite generated /etc/pki/nw/web/web-server-cert.pem, /etc/pki/nw/web/web-server-key.pem, /etc/pki/nw/web/web-server-cert.chain and /etc/pki/nw/web/web-server-cert.p7b files with the files you renamed in step 1.
4.Restart NGINX service.service nginx restart.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-23 09:15 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-23 09:28 AM
Hi Martin,
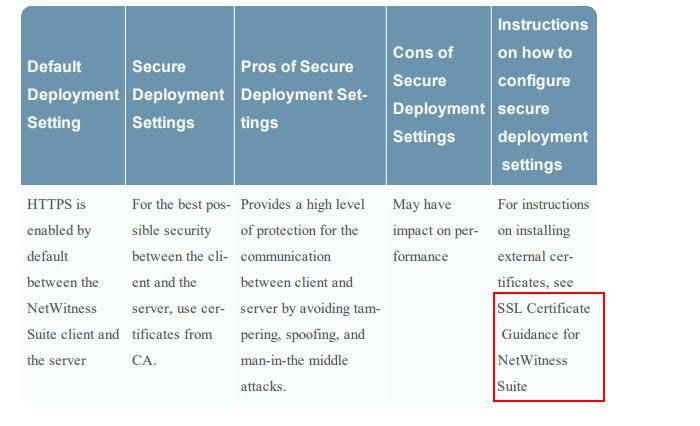
There is no process mentioned on page 61 for updating external certificates as well there is column mentioned to refer "SSL Certificate Guidance for NetWitness Suite" to upload External certificates. But I am not able to find the article for the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-23 09:37 AM
This is taken from the security config guide. I can confirm that this works perfectly.
1.Rename your certificate files and save them in for NGINX.
Rename the customer provided cert.pem certificate pem file to web-server-cert.pem.
Rename the customer provided key.pem key pem file to web-server-key.pem.
Rename customer provided cert.chain certificate chain file to web-server-cert.chain.
Rename cert.p7b certificate p7b file to web-server-cert.p7b.
2.SSH to the NW Server.
3.Replace the existing NetWitness Suite generated /etc/pki/nw/web/web-server-cert.pem, /etc/pki/nw/web/web-server-key.pem, /etc/pki/nw/web/web-server-cert.chain and /etc/pki/nw/web/web-server-cert.p7b files with the files you renamed in step 1.
4.Restart NGINX service.service nginx restart.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-23 09:41 AM
Sean's steps are correct. It would appear that the document has since been changed since I last interacted with it. I apologize for that. I am currently looking for their new location.
Thanks Sean.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-24 03:44 AM
Hi Aaron & Sean,
Thanks for the steps, that would be much more useful., I was provided with with a certificate in .crt form which I can convert to .pem form
/etc/pki/nw/web/web-server-cert.pem-- this is for server certificate
/etc/pki/nw/web/web-server-key.pem, -Key for server certificate
/etc/pki/nw/web/web-server-cert.chain - Root & Intermediate certificate?
/etc/pki/nw/web/web-server-cert.p7b- what would this be?
Please clarify whether I am correct ? Also, would it be Okay, If I have no Key certificate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-07-24 09:32 AM
You'll need the key. The p7b is a bundle contains the certificate and any chain certificates that exist. No key is included in this bundle.
And I must add that you should backup the /etc/pki/nw/web/ files before you replace them up.
If your organization has a certificate authority, you can probably show them these instructions and they should be able to get exactly what you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-09-20 05:54 AM
Hi I have added the root Certificate as well as the server certificate as suggested, but still it is showing me Not secure option as below. Its not showing any Invalid Ceritificate as well.. Then how can I remove this insecure thing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-09-21 05:06 PM
It might be an issue with the cert not being part of your OS's and/or browser's trusted certificate store. You can import your server cert and your CA cert and see if those help resolve this.
And fwiw, in my lab I have run through this process and Firefox shows everything Secure/Green, but Chrome does not.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-09-24 05:27 AM
We should include Subject Alternative Name into the certificate when we generate the same.
For Chrome 58 and later, only the subjectAlternativeName extension, not commonName, is used to match the domain name and site certificate. The certificate subject alternative name can be a domain name or IP address.