- NetWitness Community
- Discussions
- Using payload meta and analyzing DNS requests
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-03-31 12:53 PM
Original Thread: Searching for a specific packet size
have a use case to monitor DNS payloads for irregularities.
Is it possible and appropriate to use the following app rule syntax to find any DNS packet/session where the payload is over 100 bytes. (Per IETF max DNS payload per protocol is 512 bytes)
service = '53' && payload = 100-u
I see the info above in the thread about using tag = l-10000 for less than 10k, but not sure on format for greater than.
Thanks for your help!
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-01 08:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-01 08:10 AM
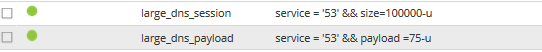
Answer with an example for you ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-07 10:23 AM
Thank you very much Mr. Partington!

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-07 12:24 PM
Does this make sense?
My understanding is that the payload one will show me a single DNS packet that has larger than 75 bytes. And the first should look at any sessions that are over 100kb and match DNS service type.
The bytes.ratio recommendation above shows the syntax which is very helpful, but I'm a little confused where these meta keys come from:
size
payload
bytes.ratio
Is this created via Lua parsers? Which one? Custom?
I bet I need to get at a low-level and create my own Lua parsers at some point but would rather NOT do that yet. Looking for quick wins with this product for content output for my IR team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-08 10:26 AM
bytes.ratio is a custom meta key from an internal content back (used that as an example of the upper and lower bounds syntax) which is filled by a custom parser.
You might also want to use this apprule as well to catch tcp 53 and large session (in case something is using that port but is not actually dns traffic)
name=large_session_dns_port rule="tcp.dstport = 53 && size=100000-u
If you haven't already set directionality application rules I would investigate that as well so you can add direction to these alerts ( dns_large session and outbound traffic direction).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-08 11:35 AM
Yep I do have custom directional rules in place.
Thanks for the tip for tcp.dstport, I also have another app rule in place for service = '53' && tcp.dstport != '53'
Thanks again Eric for all your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-04-08 11:44 AM
If you take a look at the details for the dns_verbose_lua parse in RSA Live there are other details that might be useful to you and your IR team. These were recently added to most but not all parsers.
risk.warning
* anomalous or non-dns session on dns port
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-02-10 10:14 AM
Kevin,
I am surprised I hadn't seen this post earlier...but better late than never.
The meta keys txbytes, rxbytes and bytes.ratio came from the IR_1_txrxBytes.lua parser. I wrote this parser when someone had asked the question about which side sent more data. The bytes.ratio is the calculation of transmit to receive bytes. It would have a score of 0-100. A score of 0 would mean more data was received than transmitted. Conversely, a score of 100 means more data was transmitted than received.
My intent was to do more analysis around these ratios of data sent and received.
Please note that the content of this parser was added in session_analysis parser. The meta key names were changed.
Chris