- NetWitness Community
- Discussions
- Re: What Happens If You Visualize a Malicious PDF?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
What Happens If You Visualize a Malicious PDF?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-01-29 10:04 AM
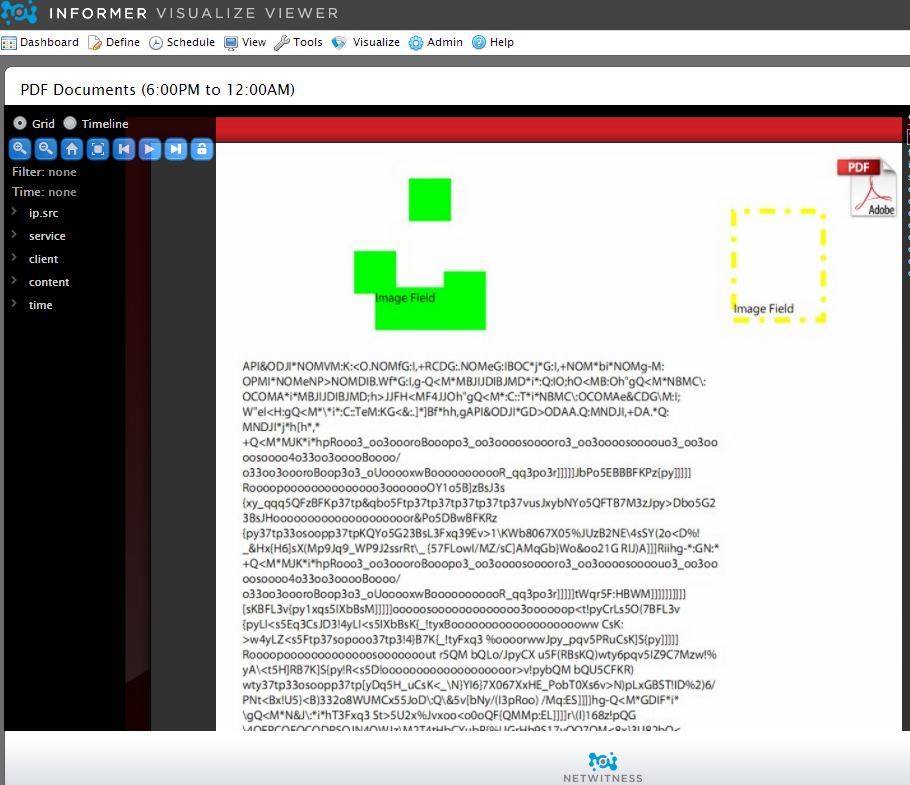
The Informer's Visualize service uses Microsoft Silverlight to display documents as images. So if you encounter a malicious PDF document that contains exploit code, many people get worried that they might be exploited themselves. There is no exploit, but the PDF actually stands out amongst a cluster of normal documents. Check out the screenshot:
What makes this document stand out is the gibberish on the page. This document was extracted when someone visited a malicious website, hit malicious javascript and got redirected to this document. In a collection of 75 PDF's, this stands out pretty well due to its malformation. Not every malicious PDF document will reconstruct well in Visualize, but when they do it makes them pretty easy to spot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-02-07 07:38 AM
I am a veteran IPS consultant and I kind of disagree there..If the pdf contains a shell code, the moment it is parsed by the program, the shell code is executed...This results in giving access to the appliance to the hacker waiting to listen for the execution of the shellcode.I am aware about the spectrum.
Well if it is capable of intercepting shellcodes, which I believe is not easy then the appliance can contain the shellcode making it a sandbox to showcase the pdf.
Having said that, I am a fresher to netwitness and SA, so if I am missing something, please guide me and forgive my ignorance.Would spectrum mitigate it or something...
Another quick question is - I need to know what is the difference between log decoder and decoder..
cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-02-07 09:03 AM
Agentnetwit, you don't seem to understand how our file extraction works. We extract millions of artifacts of malware, viruses and trojanized documents daily and it does not nor cannot impact our appliances. We reassemble these artifacts from the binary layer and provide a path for download and analysis of those artifacts. True, if you choose to foolishly run or execute those malicious artifacts on an unprotected and vulnerable desktop, the code could deliver its payload. Our research team actually deliberately does this often to determine how malware behaves on a network.
But Visualize, as mentioned in the first sentence above, presents documents as images. Visualize does not use the application layer of these document types to open the documents. By bypassing vulnerable applications an analyst can see embedded shellcode in the document, as presented above.
A log decoder aggregates logs using our metadata framework. Packet decoder aggregates network capture using the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-02-07 10:17 AM
Thanks,
(log decoder aggregates using the metadata)
I thought the concentrator does that, can you help us with the clear difference..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-02-07 10:23 AM
Decoders create the metadata. Concentrators are the query platform.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-02-07 04:35 PM
We extract millions of artifacts of malware, viruses and trojanized documents daily and it does not nor cannot impact our appliances. We reassemble these artifacts from the binary layer and provide a path for download and analysis of those artifacts.
So I guess it is using community intelligence, file content to mitigate these attacks.
Our research team actually deliberately does this often to determine how malware behaves on a network.
so basically it is sandboxing and performing network-behavior analysis..
Visualize does not use the application layer of these document types to open the documents. By bypassing vulnerable applications an analyst can see embedded shellcode in the document, as presented above.
This is a little hard to conceive that without looking at the application layer, it is looking "in" the document to see the shellcodes..How is this possible? This is a 2 part question-
1.Can you plz explain with an example..
2.How would this scenario address zero day attack?
Lastly, Does it address OWASP Top 10 attacks also?
I am just gathering more and more information about this product which I would be suggesting to companies and implementing them as well...
Many thanks in Advance Fielder..Appreciate your responses....