- NetWitness Community
- Products
- NetWitness Platform
- Advisories
- Product Advisories
- Threat Detection Content Update - July 2018
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Threat Detection Content Update - July 2018
Summary:
Several changes have been made to the Threat Detection Content in Live. For Added detection you need to add/subscribe to the content via Live, for retired content you'll need to manually remove those, and for additional changes no action is required if you are subscribed to content.
Additions
Hunting
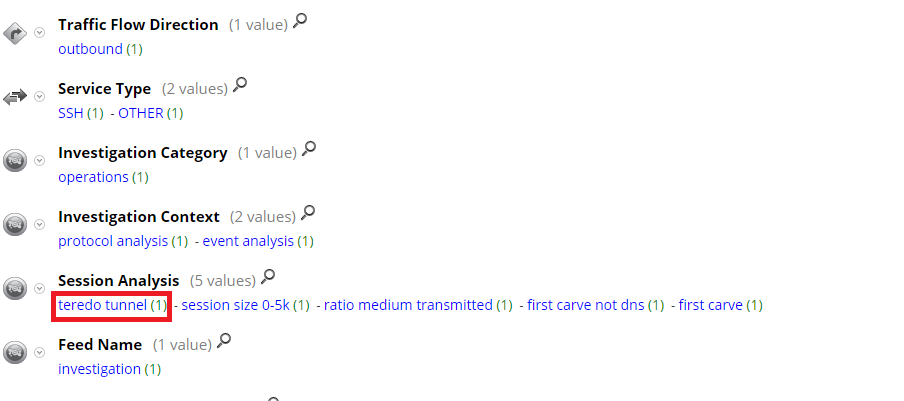
- Packet parser: Teredo detection - The transition to Internet Protocol version 6 (IPv6) has opened up a whole new range of communication vectors that allow attackers to set up covert communication channels across networks. Teredo is a transition technology that gives full IPv6 connectivity for IPv6-capable hosts that are on the IPv4 Internet but have no native connection to an IPv6 network. Teredo Tunneling comes with various security issues that should be kept in mind before it is deployed in the network.
- Attack Surface - Teredo Tunneling increases the attack surface as it assigns routable IPv6 address to otherwise non-routable devices which are sitting behind a NAT device. Thus Teredo increases exposure of complete IPv6 stack and tunneling software to attacks.
- UDP on Firewall - Since Teredo embeds the IPv6 traffic inside UDP packets and then transmits them within IPv4 packets, UDP traffic must be allowed on the firewall to allow Teredo to work.
- DoS on Teredo Clients - Since Teredo clients use mapped address and ports from Teredo servers, this service must be protected from malicious 3rdparty servers which act as Teredo servers and send crafted malicious inputs to Teredo clients. In order to prevent spoofing, the Teredo clients perform a relay discovery procedure by sending an ICMP echo request to the native host.
- DDoS on Teredo Relay - Since Teredo Relay acts as a relay for IPv6 packets, this service must be protected against crafted packets that can be used by attackers to hide their address and conduct a Denial of Service attack.
New Teredo lua parser can identify Terrdo tunnels on in network traffic to give more visibility and helps prioritize threat hunting capabilities.
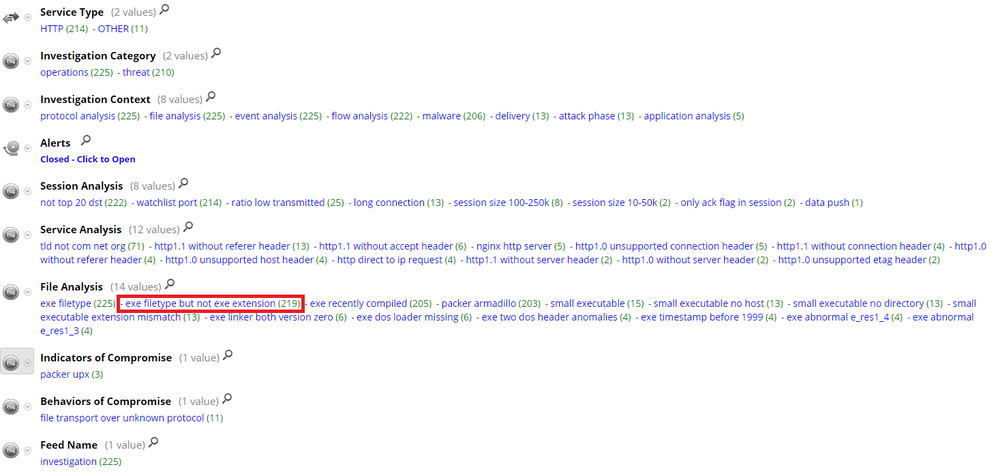
- App rule: exe filetype but not exe extension - This application rule alerts if an executable was detected in the session but no filename with an "exe" extension was seen in the same session. This will act as additional indicator while hunting if different file extension is harvested to evade firewalls and IDS/IPS rules which looks for and blocks “.exe” files.
- RSA NetWitness Endpoint Insights - Four new reports are added to take advantage of the Endpoint Scan Data collected by either the free RSA NetWitness Endpoint Insights agent, or the full RSA NetWitness Endpoint 4.4 meta integration. Analyst can Use these reports to gain summarized visibility into endpoints, and to prioritize hunting efforts through outlier/stack analysis.
- Detailed information and screenshots about reports can be found here: https://community.rsa.com/community/products/netwitness/blog/2018/05/18/netwitness-endpoint-integration-starter-reports-and-dashboards
- Endpoint Machine Summary Report - This report shows information for the machines configured to run the RSA NetWitness Endpoint agent including an OS and endpoint version summary.
- Endpoint Scan Data File and Process Outliers Report - This report focuses on rarity of particular process, file, and autorun features in the environment.
- Endpoint Scan Data Autorun and Scheduled Task Report - This report looks for suspicious autoruns and tasks using a few key features. Autoruns/Scheduled Tasks mechanisms are often used by attackers to maintain persistence on a compromised host. This is not an exhaustive set of potentially suspicious autorun behavior, but should give an analyst visibility into some of the more common techniques leveraged by attackers.
- Endpoint Scan Data Host Report - This rule will return information about the endpoint for the configured hostname. This information could be useful when conducting an investigation into a suspect machine. Information includes autoruns, tasks, machine details, processes, services, DLLs and files.
- Detailed information about endpoint content can be found here: https://community.rsa.com/community/products/netwitness/blog/2018/05/18/rsa-netwitness-endpoint-content-dashboards-esa-rules
- Endpoint Insights Configuration Guide for Version 11.1 can be found here: https://community.rsa.com/docs/DOC-86450
- Training on RSA NetWitness Endpoint, including analysis of Scan Data, may be found on RSA Link: https://community.rsa.com/docs/DOC-84977
- Packet parser: SMTP_lua Options - Options Lua file has been added to alter the behavior of the SMTP_lua parser. With new options file, analysts can register source and destination email address differently to improve detection and analysis capabilities.
Changes
Hunting
- HTTP_lua - Updates were made in HTTP_lua parser to extract values of originating IP addresses from a request header block. Update has been made for efficient querying on orig_ip meta key and avoid confusion between CDN IPs and source IPs from both request and response headers.
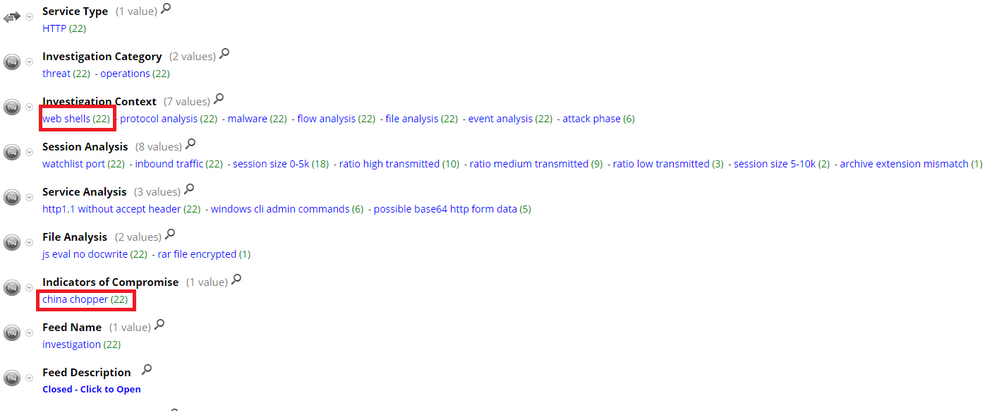
- china_chopper - Updates are made to this parser to detect new versions of china chopper web shell. China Chopper is a webshell used to remotely access Windows or Linux servers. It is malicious software used by the bad guys. This parser detect existence of malicious webshell in network traffic.
Retired
We strive to provide timely and accurate detection of threats as well as traits that can help analysts hunt through network and log data. Occasionally this means retiring content that provides little-to-no value
- Following Correlation Rules have been discontinued, due to them having little investigative value and limited correlation options:
- `IPV4 Potential DB Server Sweep
- IPV6 Potential DB Server Sweep
- IPv4 Horizontal Port Scan 5
- IPv6 Horizontal Port Scan 5
- IPv4 Vertical TCP Port Scan 5
- IPv4 Vertical UDP Port Scan 5
- IPv6 Vertical TCP Port Scan 5
- IPv6 Vertical UDP Port Scan 5
- IPv4 Potential Web Sweep 10
- IPv6 Potential Web Sweep 10
- IPv4 Bulk Data Transfer 20 Mb
- IPV6 Bulk Data Transfer 20 Mb
- IPv4 Bulk Data Transfer 50 Mb
- IPV6 Bulk Data Transfer 50 Mb
- Windows Automated Explicit Logon
- Following app rules are discontinued because there is no longer active support for this rule, and thus it will never trigger. Signatures for these rules are deprecated over time.
- NJRAT Acquisition
- jRAT Download
- Remote Control Client Download
For additional documentation, downloads, and more, visit the RSA NetWitness Platform page on RSA Link.
EOPS Policy:
RSA has a defined End of Primary Support policy associated with all major versions. Please refer to the Product Version Life Cycle for additional details.
- Advisory
- Announcement
- logs & network
- logs and network
- NetWitness
- netwitness logs
- netwitness logs & network
- netwitness logs & packets
- netwitness logs and network
- netwitness logs and packets
- netwitness network
- netwitness packets
- netwitness suite
- NW
- NWP
- Product Advisory
- product announcement
- Product Communication
- Product Notification
- release announcement
- RSA Live Content
- RSA NetWitness
- RSA NetWitness Platform
- sa
- SCOL Note
- Security Analytics
In this article
Related Content