This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Platform Product Advisories
Read and subscribe to the latest announcements and advisories relating to the NetWitness Platform.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- NetWitness Community
- Products
- NetWitness Platform
- Advisories
- Product Advisories
- Threat Detection Content Update - May 2018
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Threat Detection Content Update - May 2018
Threat Detection Content Update - May 2018
Summary:
It's been a while since our last update, but we've been hard at work. Several changes have been made to the Threat Detection Content in Live. For Added detection you need to add/subscribe to the content via Live, for retired content you'll need to manually remove those, and for additional changes no action is required if you are subscribed to content.
Additions:
Detection
- User and Entity Behavior Analytics (UEBA) Essentials Content Pack (Live Bundle) (https://community.rsa.com/docs/DOC-86973)
- The purpose of UEBA and user-hunting is to detect or bring focus to suspicious user and entity behavior to find potential insider threats, lateral movement by external attackers, or general abuse/misuse of user accounts. Deploying this bundle will download all of the content and content dependencies of the UEBA Pack to the services appropriate for each content type.
- User and Entity Behavior Analytics (UEBA) Hunting Guide (https://community.rsa.com/docs/DOC-86470)
- UEBA Hunting Guide helps to flush out use cases and build effective detection and hunting content, using User and Entity Behavior Analytics. Sample hunt cards are included that provide insight on what you can do to verify user anomalies. Additionally the content is aligned with various Mitre ATT&CK techniques.
- [UEBA Essentials] ESA rules are updated to add UBA functionality with Context Hub list for 11.1+
- UEBA functionally helps evaluate ability to detect, prioritize, and respond to various threats. There are multiple use cases which are addressed by all these updated ESA rules with UEBA capabilities.
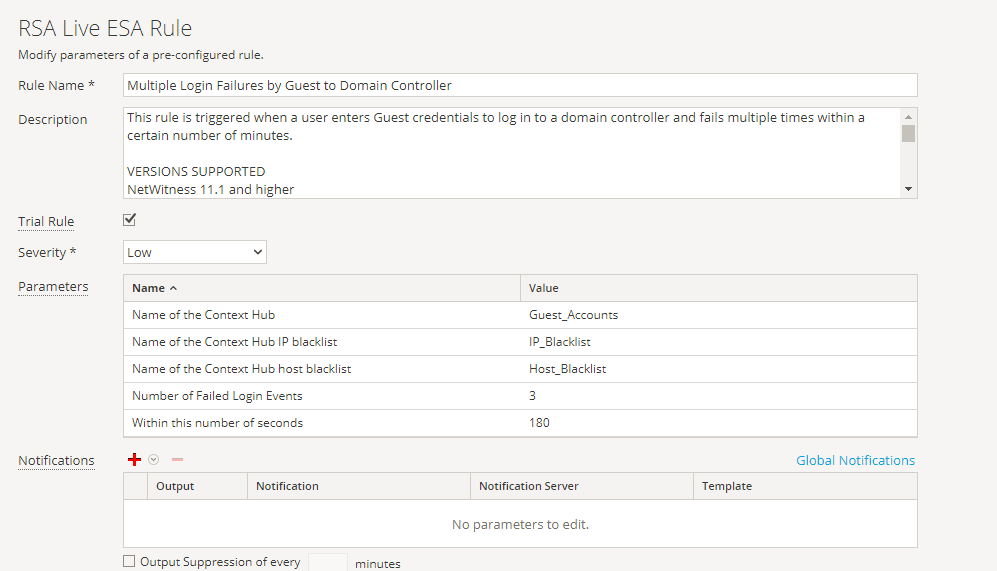
- The following ESA rules addresses use cases where attacker using employee account is trying to brute force to get in or compromised user credentials which is undoubtedly the biggest use case for UEBA. With these rules analyst should be able to easily detect if hackers have control of a network user’s credentials, regardless of attack vector or malware. This detection works across the combination of a user’s account credentials, devices, or IP addresses. Analyst can configure user accounts, devices and IP address along with number of alerts and time window according to severity of infrastructure. It also deals with use cases where account are being shared with multiple users. For example, a group of DBAs might share an account in the customer database to repair issues, tune for performance, etc. The UBA should be able to identify these cases, indicate which users were sharing the accounts, and support streamlined remediation.
Analyst can investigate more using investigate and respond to determine whether alert was due to a simple “fat fingered” mistake or was a sign of an attempted account takeover and if its takeover attempt, was it successful or not. Done effectively, the UBA could save lot of hunting hours at a larger organization.- Multiple Login Failures by Guest to Domain Controller
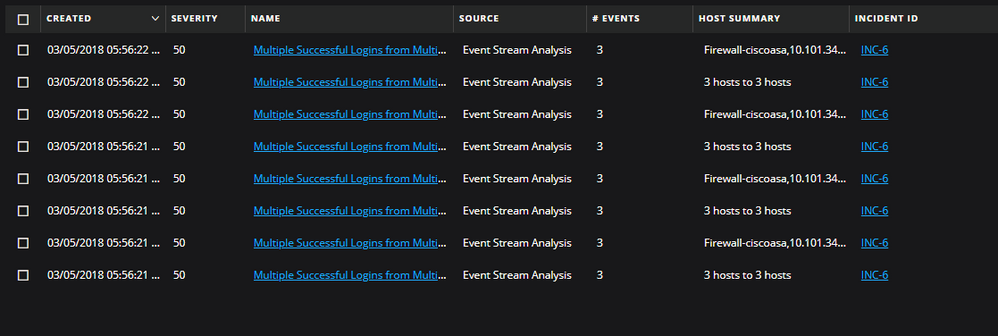
- Multiple Successful Logins from Multiple Diff Src to Diff Dest
- Multiple Failed Logins from Same User Originating from Different Countries
- Multiple Failed Logins from Multiple Users to Same Destination
- Multiple Successful Logins from Multiple Diff Src to Same Dest
- Multiple Failed Logins from Multiple Diff Sources to Same Dest
- Failed logins Followed by Successful Login and a Password Change
- Multiple Failed logins Followed by Successful Login
- Multiple Account Lockouts from Same or Different Users
- Logins across multiple servers
Showing off the Context Hub List configuration
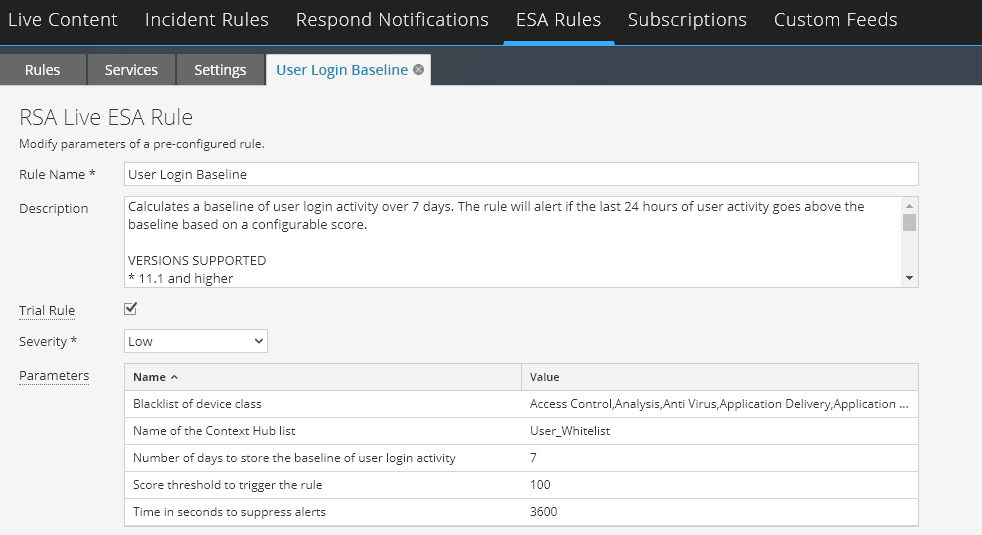
- The following rules are designed to alert if a user account is suspected of misuse due to credential compromise or a malicious insider and that user is attempting to laterally move across the organization. User Baseline rule calculates a baseline of user login activity over 7 days and will alert if the last 24 hours of user activity goes above the baseline based on a configurable score.
These rules mainly addresses use cases such as insider threat, dormant accounts. They should be able to detect when a user, privileged or not, is performing risky activities that are outside his or her normal baseline. The UEBA Essentials solution provide continuous visibility into employees and contractors that have not used their credentials over a predefined period or users who haven’t logged into their accounts within 30 days or that may have left the company, and normal processes have not caused the account to be deactivated.- User Login Baseline
- Insider Threat Mass Audit Clearing
- Failed logins outside of business hours
- Direct Login by a Watchlist Account
- The following updated rules address use cases such as privileged user compromise or executive assets accessed. The compromise of a privileged user’s (e.g. DBA or system admin) credentials can be more difficult to detect. Successful attacks on a privileged account can cause serious damage to an organization. Executive assets such as the CEO or CFO’s laptop are obvious targets for hackers. These systems contain sensitive earnings, M&A, or competitive information. As an example, hundreds of millions of dollars are stolen each year, via wire transfers driven by webmail schemes that trick company executives into approving these transfers.
The UEBA Essentials solution can help identify specific attacks on privileged users, who have special access to sensitive systems. Attackers gain privileged user credentials and then access key systems directly; these rule's UEBA capabilities should detect and alert on such events immediately.- Multiple Login Failures by Administrators to Domain Controller
- Multiple Failed Privilege Escalations by Same User
- Suspicious Privileged User Access Activity
- Privilege Escalation Detected
- Privilege User Account Password Change
- User Added to Admin Group Same User Login OR Same User su sudo
- The following ESA rules address general use cases related to UEBA such as attempted lateral movement, privileged escalation, account creation, sharing, and modifications.
Hackers often enter a network via malware on one system, then use that initial entry to create new accounts that are unrelated to the entry account. Even after re-imaging the initial compromised machine, the hackers are already in the system and using new credentials. An attacker tries to move laterally compromising multiple systems on same network or same group.
With the UEBA capabilities an analyst will be able monitor account creations, modifications, behaviors and quickly identify anomalous activities such as unauthorized credential creation or procedural violations.- krbtgt Account Modified on Domain Controller
- Lateral Movement Suspected Windows
- User Added to Administrative Group + SIGHUP Detected within 5 Minutes
- Windows Suspicious Admin Activity: Shared Object Accessed
- Windows Suspicious Admin Activity: Network Share Created
- Windows Suspicious Admin Activity: Firewall Service Stopped
- Windows Suspicious Admin Activity: Audit Log Cleared
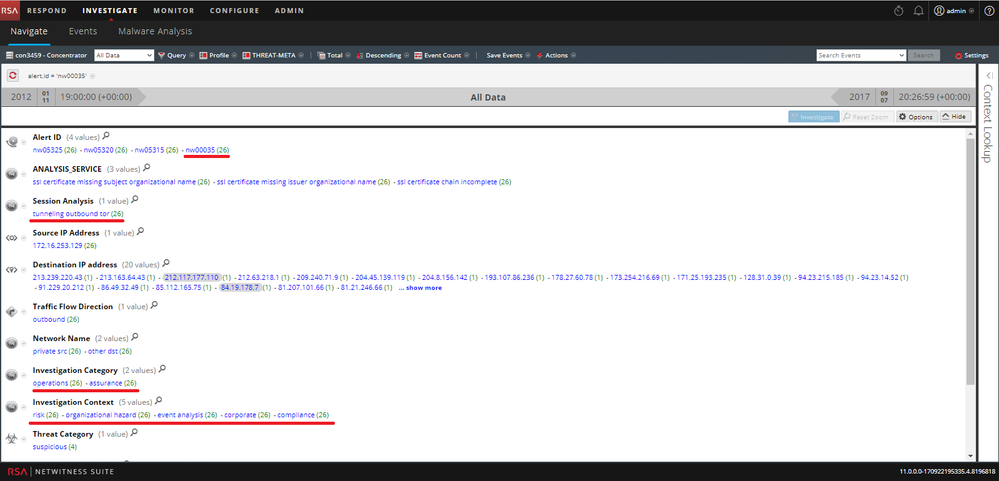
- Tor traffic detection:
- Event Stream Analysis Rule for Outbound Tor rule to indicate that Tor outbound traffic have been detected.
- Application Rule for Tor Outbound which detects an encrypted network sessions as well as log sessions to an external (non RFC-1918) IP destination that shows at least one indicator of using the Tor protocol for anonymous data access. The text: 'tunneling outbound tor' will appear in the 'analysis.session' meta-key.
Changes
Detection
- Update for Internal Data Posting to 3rd Party Sites ESA Rule for detecting particular pattern in traffic between internal systems to 3rd party sites. The rule now uses the traffic flow parser to determine direction as well as has a whitelist for 'alias.host' so you can filter out hostnames you don't want to be altered on.
- Update for Horizontal Port Scan ESA Rule for more accurate detection by using 'payload = 0' to help reduce false positives. Additionally, two 'Horizontal Port Scan' rules were retired (noted below).
Hunting
- HTTP_lua - Updated with the additional functionality of noting when a session contains a single request and response response. Additionally added web-socket identification and the parser attempts to extract usernames and passwords from query strings when present. An option in the HTTP_lua options file is now available to parse out custom HTTP header values and put them in a define meta-key.
- phishing_lua - Updates were made to identify phishing source and output, HTML_threat and rtmp output to fine tune parsing. This parser now tries to extract host even if no schema is present.
- session_analysis_lua - Functionally has been added into session analysis parser various flag combinations that can help highlight suspicious connections for various scan types, etc... Xmas and NULL Session, Host Not Listening, Session Teardown, All TCP Flags Set, SYN with No Response, and Data Push are all called out in 'session.analysis. now.
- fingerprint_pdf_lua - This parser was updated to better detect and extract URLs for further analysis by analyst to identify potential source and attack vectors.
- MAIL_lua - Improvements were made to accommodate non-RFC-compliant mime boundaries and full name extraction.
- Nwll_lua - Some functions were rewritten/modified to help support parser changes in the pipeline.
Retired
We strive to provide timely and accurate detection of threats as well as traits that can help analysts hunt through network and log data. Occasionally this means retiring content that provides little-to-no value.
- The Event Stream Analysis (ESA) Rules mention below are discontinued since they are now implemented with CH Lists for UBA
- Multiple Login Failures by Guest to Domain Controller
- Multiple Successful Logins from Multiple Diff Src to Diff Dest
- User Login Baseline
- krbtgt Account Modified on Domain Controller
- Lateral Movement Suspected Windows
- Multiple Login Failures by Administrators to Domain Controller
- Insider Threat Mass Audit Clearing
- Multiple Failed Privilege Escalations by Same User
- Suspicious Privileged User Access Activity
- Multiple Failed Logins from Same User Originating from Different Countries
- User Added to Administrative Group + SIGHUP Detected within 5 Minutes
- Multiple Failed Logins from Multiple Users to Same Destination
- Multiple Successful Logins from Multiple Diff Src to Same Dest
- Multiple Failed Logins from Multiple Diff Sources to Same Dest
- User Added to Admin Group Same User Login OR Same User su sudo
- Direct Login by a Watchlist Account
- Windows Suspicious Admin Activity: Shared Object Accessed
- Windows Suspicious Admin Activity: Network Share Created
- Windows Suspicious Admin Activity: Firewall Service Stopped
- Windows Suspicious Admin Activity: Audit Log Cleared
- Failed logins Followed by Successful Login and a Password Change
- Privilege User Account Password Change
- Privilege Escalation Detected
- Multiple Failed logins Followed by Successful Login
- Multiple Account Lockouts from Same or Different Users
- Logins across multiple servers
- Failed logins outside of business hours
- The following ESA rules are discontinued and replaced by the new 'Horizontal Port Scan'
- Port Scan Horizontal Packet
- Port Scan Horizontal Log
- AIM_lua parser is discontinued since AOL Instant Messenger products and services have been shut down and no longer work.
- App Rule ‘Direct to IP HTTP Request’ is discontinued and replaced by logic in the HTTP Lua parser.
Other Bug Fixes and Changes
- HTTP_lua - Bug fixes to improve header detection and extraction.
- LDAP - Parser now parses out username and password only on port 389
EOPS Policy:
RSA has a defined End of Primary Support policy associated with all major versions. Please refer to the Product Version Life Cycle for additional details.
Tags (26)
- Advisory
- Announcement
- logs & network
- logs and network
- NetWitness
- netwitness logs
- netwitness logs & network
- netwitness logs & packets
- netwitness logs and network
- netwitness logs and packets
- netwitness network
- netwitness packets
- netwitness suite
- NW
- NWP
- Product Advisory
- product announcement
- Product Communication
- Product Notification
- release announcement
- RSA Live Content
- RSA NetWitness
- RSA NetWitness Platform
- sa
- SCOL Note
- Security Analytics
No ratings
In this article
Related Content

© 2022 RSA Security LLC or its affiliates. All rights reserved.