- NetWitness Community
- Products
- NetWitness Platform
- Advisories
- Product Advisories
- Threat Detection Content Update - September 2018
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Threat Detection Content Update - September 2018
Summary:
Several changes have been made to the Threat Detection Content in Live. For added detection you need to deploy/download and subscribe to the content via Live, for retired content you'll need to manually remove those.
Additions:
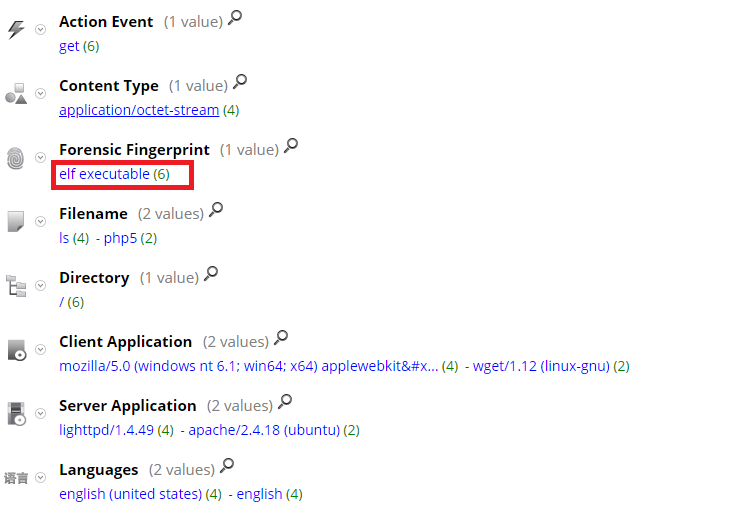
fingerprint_elf Lua Parser – New parser is released to detect elf executable files for Linux based machines. The ELF file format allows a Linux program to specify an arbitrary loader, which is responsible to load and prepare the executable in memory. Most Linux based malware families uses different manipulation techniques with ELF executable binaries. With fingerprint_elf parser, analysts can now detect ELF executable files on the network which will help in investigation of different Linux based incidents.
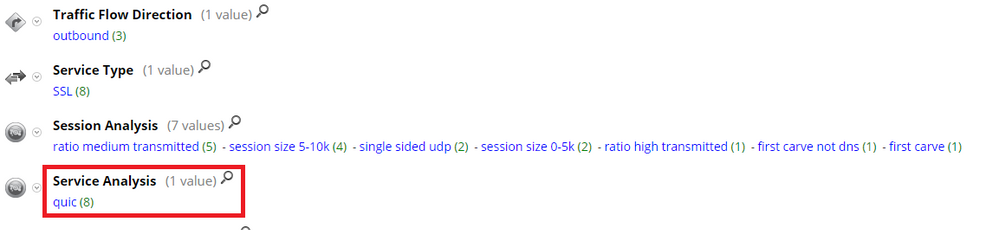
QUIC Lua Parser - New parser is introduced to detect traffic over QUIC protocol. QUIC is a secure transport protocol developed by Google and implemented in Chrome in 2013, currently representing one of the most promising solutions to decreasing latency while intending to provide security properties similar with TLS. Analyst can detect usage of quic protocol on wire for better visibility and investigation.
teamviewer Lua parser – New parser is now available on Live to identify TeamViewer sessions. Identifying TeamViewer activity on enterprise network can be point of interest to analyst because anomalies can use TeamViewer for remote desktop connection to take control remotely.
phishing_lua Options – Option file is introduced for phishing_lua parser. Using optional parameters analysts can alter the behavior of the phishing_lua parser. It gives options to whitelist domains, register URL components, deduplicate host registration, host consistency etc.
Detailed documentation for Phishing Lua Parser Options
Changes:
HTTP_lua – Functionally has been added to HTTP_lua parser to detect x-sinkhole headers for better hunting and investigation experience. x-sinkholes headers can be an indication of malware sinkhole traffic on the wire. Attackers and malware authors try to blend in with regular network communications. Establishing interactive sessions versus mechanical sessions aids in identifying a malware behavior's bidirectional communications. Analyst can initiate further in-depth investigation for ioc:malware sinkhole.
traffic_flow Lua parser – IPv6 support has be added to traffic_lua parser to provide subnet names for internal networks, and directionality of the session (inbound, outbound, lateral). It add lot more visibility to analyst using IPv6 as default internal protocol.
Detailed documentation for Traffic Flow Lua Parser
ntp_lua – This parser is updated for efficiency improvements as well as added detection for more session such as single sided NTP sessions.
TLS_lua – Updates were made to enhance identification to sessions where there are two streams but the other stream contains no payload which will give analyst more visibility on TLS sessions.
Retired:
We strive to provide timely and accurate detection of threats as well as traits that can help analysts hunt through network and log data. Occasionally this means retiring content that provides little-to-no value.
Malware domain feed – Feed has been marked discontinued because RSA Netwitness Platform no longer licenses www.malwaredomains[.]com feed.
For additional documentation, downloads, and more, visit the RSA NetWitness Platform page on RSA Link.
EOPS Policy:
RSA has a defined End of Primary Support policy associated with all major versions. Please refer to the https://community.rsa.com/docs/DOC-40387 for additional details.
- Advisory
- Announcement
- logs and network
- netwiness
- NetWitness
- netwitness logs & netwitness
- netwitness platfrom
- netwitness*
- NW
- NWP
- Product Advisory
- product announcement
- Product Communication
- Product Notification
- release announcement
- RSA Live Content
- RSA NetWitness
- rsa netwitness logs and packets
- RSA NetWitness Platform
- sa
- scol notes
- security analyitcs
- threat content
In this article
Related Content