- NetWitness Community
- Discussions
- I need to clone an ESA Rule "Web DoS Attack"
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2022-02-21 08:36 AM
I need/want to clone ESA rule "Web Dos Attack". We would like to keep the default rule, and create clone one for tuning by Intel Analysts.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2022-02-21 07:43 PM
Hello EdPadilla
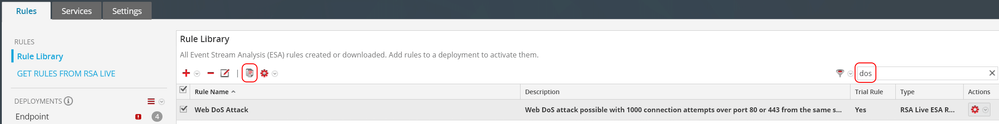
You can create a copy of the ESA Rule in the NW UI, Configure > ESA Rules
In the Rules tab > Rule Library
Find the "Web DoS Attack" rule and click on the "Duplicate a Rule" button.
Now you can edit the duplicate copy of the rule, whilst keeping the original.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2022-02-23 11:48 AM
The syntax is based on Esper. You will documentation here: https://esper.espertech.com/release-7.1.0/esper-reference/html/
Do you want to whitelist only your ip_dst and don't care about the source addresses it comes from?
In this case you might change the query to:
/*
Version: 3
*/
module Module_esa000030;
@Name('Module_esa000030_Alert')
@RSAAlert(oneInSeconds=0, identifiers={"ip_dst"})
SELECT * FROM
Event (
medium = 1
AND
tcp_dstport IN (80 , 443)
AND
ip_dst IS NOT NULL
AND
ip_dst NOT IN ('31.13.65.14')
).std:groupwin(ip_dst)
.win:time_length_batch(60 seconds, 1000)
GROUP BY ip_dst
HAVING count(*) = 1000
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2022-02-21 07:43 PM
Hello EdPadilla
You can create a copy of the ESA Rule in the NW UI, Configure > ESA Rules
In the Rules tab > Rule Library
Find the "Web DoS Attack" rule and click on the "Duplicate a Rule" button.
Now you can edit the duplicate copy of the rule, whilst keeping the original.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2022-02-22 02:40 PM
Thanks the original syntax is the following:
/*
Version: 3
*/
module Module_esa000030;
@Name('Module_esa000030_Alert')
@RSAAlert(oneInSeconds=0, identifiers={"ip_src"})
SELECT * FROM
Event (
medium = 1
AND
tcp_dstport IN (80 , 443)
AND
ip_dst IS NOT NULL
AND
ip_src IS NOT NULL
AND
ip_src NOT IN ('1.1.1.1' , '2.2.2.2' , '40.66.16.130' , '35.190.72.88' , '168.149.132.64' , '23.212.73.206')
).std:groupwin(ip_src, ip_dst)
.win:time_length_batch(60 seconds, 1000)
GROUP BY ip_src, ip_dst
HAVING count(*) = 1000
;
------------------------------------------------
However i would like to add to not alert or white list ip.dst 31.13.65.14. See below syntax, but it stills does not whitelist destination IP 31.13.65.14? What is this syntax language, and where i can get the documentation. My appliances are version 11.6.1
/*
Version: 3
*/
module Module_esa000030;
@Name('Module_esa000030_Alert')
@RSAAlert(oneInSeconds=0, identifiers={"ip_src,ip_dst"})
SELECT * FROM
Event (
medium = 1
AND
tcp_dstport IN (80 , 443)
AND
ip_dst IS NOT NULL
AND
ip_src IS NOT NULL
AND
ip_src NOT IN ('1.1.1.1' , '2.2.2.2' , '40.66.16.130' , '35.190.72.88' , '168.149.132.64' , '23.212.73.206') AND ip_dst NOT IN ('31.13.65.14')
).std:groupwin(ip_src, ip_dst)
.win:time_length_batch(60 seconds, 1000)
GROUP BY ip_src, ip_dst
HAVING count(*) = 1000
;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2022-02-23 11:48 AM
The syntax is based on Esper. You will documentation here: https://esper.espertech.com/release-7.1.0/esper-reference/html/
Do you want to whitelist only your ip_dst and don't care about the source addresses it comes from?
In this case you might change the query to:
/*
Version: 3
*/
module Module_esa000030;
@Name('Module_esa000030_Alert')
@RSAAlert(oneInSeconds=0, identifiers={"ip_dst"})
SELECT * FROM
Event (
medium = 1
AND
tcp_dstport IN (80 , 443)
AND
ip_dst IS NOT NULL
AND
ip_dst NOT IN ('31.13.65.14')
).std:groupwin(ip_dst)
.win:time_length_batch(60 seconds, 1000)
GROUP BY ip_dst
HAVING count(*) = 1000