- NetWitness Community
- Discussions
- Re: Automated Threat Detection for Log Decoder
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Automated Threat Detection for Log Decoder
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-05-23 04:18 AM
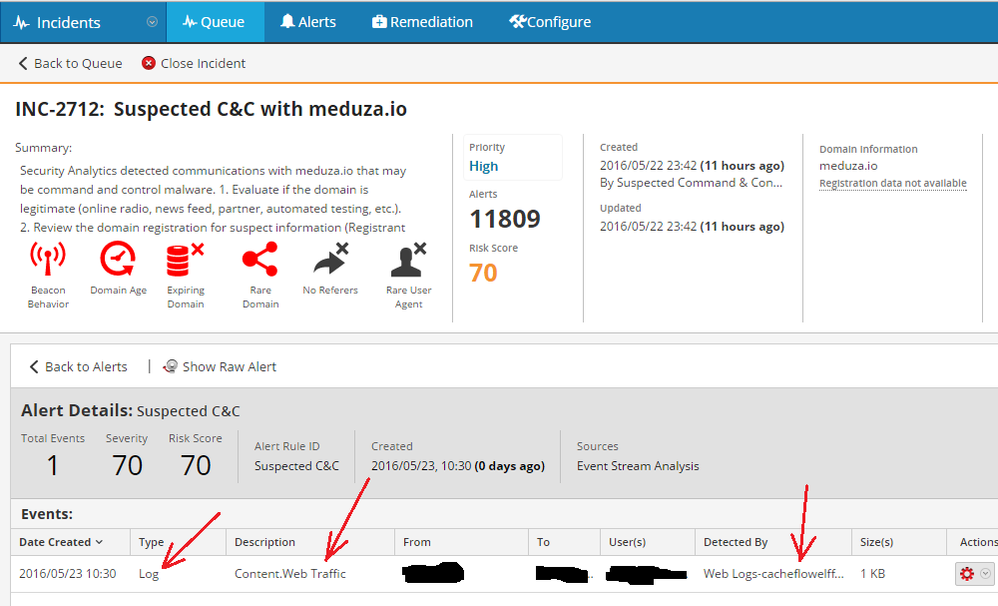
New component of ESA server Automated Threat Detection (ATD) is very promising. According to manual it analyzes HTTP packets which are parsed by the Decoder and sent to the ESA device. But if you have Log Decoder only you are out of luck (according to manual). When I asked support team of RSA about possibility to use ATD with logs from proxy device (squid, BlueCoat, etc) I received following answer:
Automated Threat Detection is an analytics engine that examines your HTTP data hence only supported for packets in combination with LUA parser.
There are no plans to expand it with logs functionality.
http://sadocs.emc.com/0_en-us/088_SA106/50_Alrt/66_C2Thrt/00_TDInfo
But all this seems strange because web proxy logs contains all necessary information.
If we look at meta from http_lua parser and contains of file /opt/rsa/esa/topology/C2.topology we can understood that following meta are analyzed by ATD:
- action (GET, POST, etc)
- ip_src
- alias_host - web domain
- client - user agent
- referer
- time
- service (must be equal 80)
Log decoder do not fill service meta, that is why ATD do not analyze logs from LogDecoder. Thats why we need to modify parser to extract required meta and inject service meta of value 80. Lets take cacheflowelff parser as an example.
1) In table-map-custom.xml we associate new xservice field with service meta
<mapping envisionName="xservice" nwName="service" flags="None" format="UInt32"/>
2) open v20_cacheflowelffmsg.xml and edit content section of GET, POST, etc message id.
So here we inject xservice field with value 80 (will be moved to service meta), extract User-Agent to agent field (will be moved to client meta), and extract referer field. Please look table-map.xml for more information about mapping fields from envision parsers to netwitness metas
content="<@xservice:80><@msg:*PARMVAL($MSG)><@fld63:*PARMVAL(username)><@fld61:*PARMVAL(h_code)><@bytes:*CALC(sbytes,+,rbytes)><@domain:*URL($DOMAIN,url)><@web_root:*URL($ROOT,url)> <@event_time:*EVNTTIME($MSG,'%W-%G-%F %N:%U:%O',fld1,fld2)><@event_source:*PARMVAL(hostname1)><@dhost:*PARMVAL(web_host)>date=<fld1>,time=<fld2>,time-taken=<processing_time>,c-ip=<saddr>,s-action=<action>,sc-status=<resultcode>,sc-bytes=<sbytes>,cs-bytes=<rbytes>,cs-method=<web_method>,cs-user=<username1>,cs-username=<username>,cs-uri-username=<username>,s-hierarchy=<h_code>,cs-host=<web_host>,rs(Content-Type)=<content_type>,cs-uri-port=<dport>,s-ip=<hostip>,r-ip=<dtransaddr>,r-supplier-ip=<fld37>,r-dns=<fld38>,c-port=<sport>,cs-category=<category>,cs-uri-scheme=<network_service>,duration=<duration>,s-supplier-ip=<daddr>,cs-auth-group=<group_object>,s-supplier-name=<fld68>,sc-filter-result=<disposition>,sc-filter-category=<filter>,cs(User-Agent)=<agent>,x-virus-id=<virusname>,s-sitename=<service>,cs-uri=<url>,cs-uri-path=<webpage>,x-exception-id=<fld88>,cs-categories=<category>,cs(Referer)=<referer>,cs-uri-query=<web_query>,cs-uri-extension=<web_extension>,cs(Cookie)=<web_cookie>,s-computername=<hostname1>,s-port=<network_port>,cs-version=<version>,cs-auth-groups=<group_object>,cs-uri-stem=<fld3>,localtime=<fld5>,x-bluecoat-application-name=<fld4>,x-bluecoat-application-operation=<fld6>,s-icap-status=<fld7>,s-icap-info=<fld8>"
3)restart logdecoder
stop nwlogdecoder && start nwlogdecoder
4) configure ATD according to manual. After 24 hours you should see some new incidents
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-05-23 07:15 PM
Hi Nikolay,
Thank you for posting this article to the community. It’s great to have passionate SA users, such as yourself experimenting with new ways to extract value out of the product. As you point out, the meta fields used by the detection model may be parsed from web proxy log events. This is actually by design as RSA does intend to release a similar model that can operate on web proxy logs. The current model however has only been certified to operate against HTTP packet data. This means that running the current model against log sources may give unexpected results compared to the same traffic captured as PCAPs. For example, the packet HTTP data is sessionized by TCP where web proxy data is made up of individual request/response transactions. This difference may require tweaks to the model in order to deliver similar detection results. So for now we do not recommend that customers attempt to utilize the model against log data in production but we would love to work with yourself and any other customers that have a lab environment in which to try out this and other experiments with SA.
Thanks,
Mark Karlstrand