What's New
The NetWitness 11.7 release provides new features and enhancements for every role in the Security Operations Center.
Note: Investigator Thick Client is no longer supported.
Upgrade Paths
The following upgrade paths are supported for NetWitness 11.7.0.0:
-
NetWitness 11.5.3.2 to 11.7.0.0
-
NetWitness 11.6.0.0 to 11.7.0.0
-
NetWitness 11.6.0.1 to 11.7.0.0
-
NetWitness 11.6.1.0 to 11.7.0.0
-
NetWitness 11.6.1.1 to 11.7.0.0
For more information on upgrading to 11.7.0.0, see Upgrade Guide for NetWitness 11.7
Security Fixes
For more information on Security Fixes, see Security Advisories.
Enhancements
The following sections are a complete list and description of enhancements to specific capabilities:
- Investigation
- Endpoint Investigation
- Concentrator, Decoder, and Log Decoder Services
- Event Stream Analysis (ESA)
- Platform
- Upgrades
- NetWitness Services
Go to the NetWitness All Versions Documents page and find NetWitness Platform guides to troubleshoot issues.
Investigation Investigation
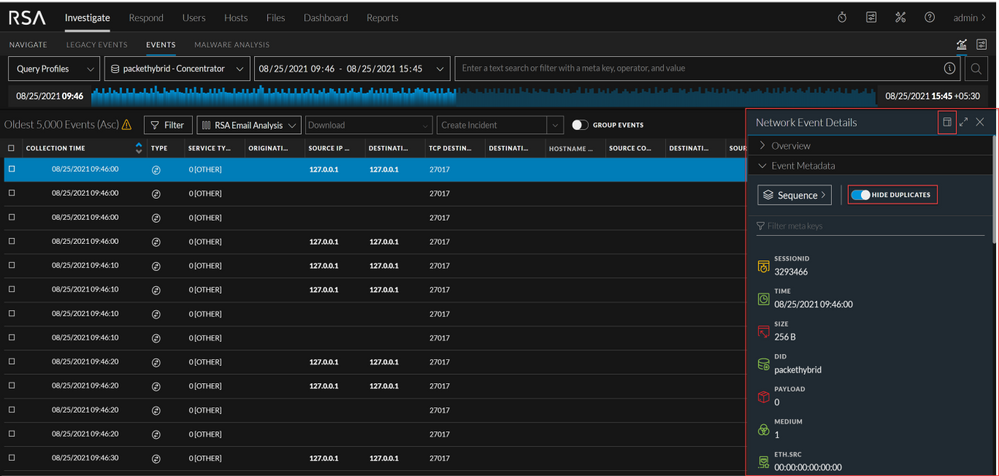
Meta Only Event Reconstruction
As analysts review events, the new compact and expanded metadata views provide an alternative workflow to only view the high-level details of the event and in use cases where no raw data is present.
Improved Broker Query Experience
Analyst queries at the top-level Broker now by default provide partial results when one of the sub-services loses connectivity or times out. In addition, a hierarchical view of what is attached to the Broker is available to analysts to exclude certain sub-services prior to query if necessary.
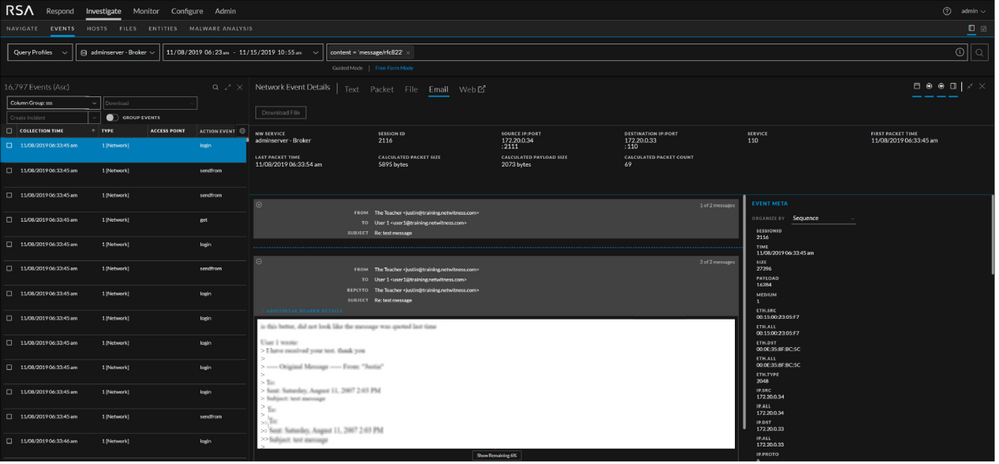
Email Reconstruction Improvement
Analyst can view the content of all the emails in a single session using the Expand All Emails option available on the Email view.
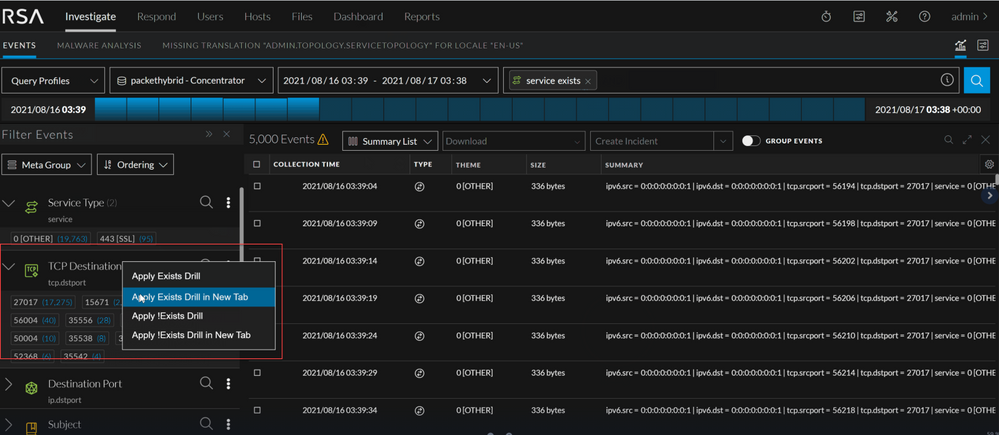
Direct Query Interaction with Meta Keys in Event Filter Panel
Analyst steps to create a query have been streamlined by clicking directly on the meta key name to generate a query with only the meta key. Alternatively, searches with combination of key value pairs are available inside the Event Filter panel without requiring direct interaction with the query bar.
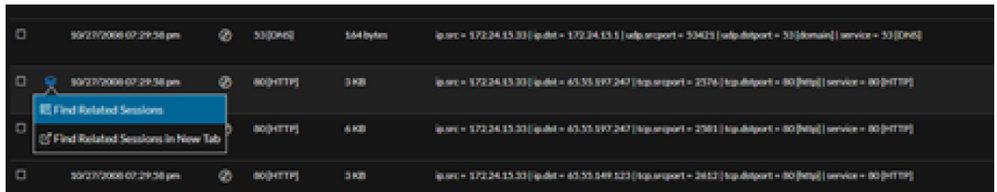
Network Fragment Identification
Analysts can view the related sessions for an event for analysis and investigation by hovering over the icon for the event.
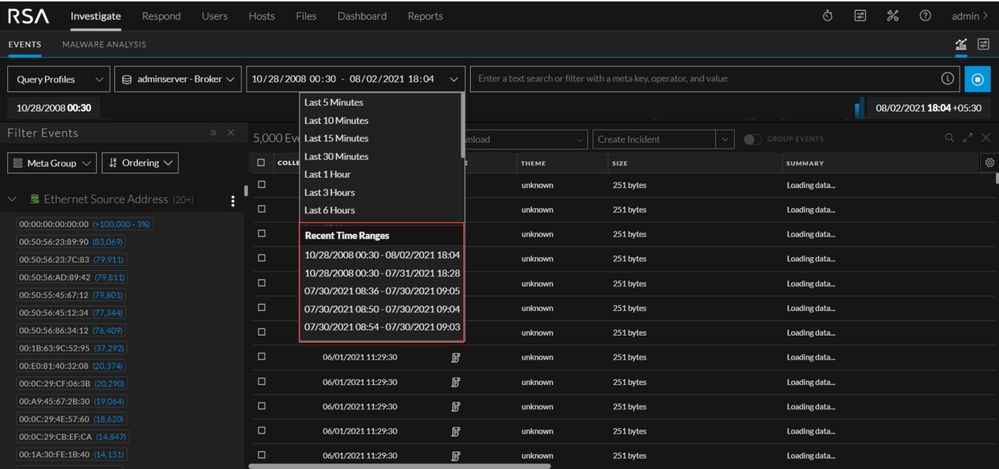
Saved Time Ranges
Analysts can take advantage of the last five recently used time ranges for future searches saving the investigation time. The saved time ranges are displayed under the Recent Time Ranges section.
For more information, see the Investigation User Guide.
Endpoint InvestigationEndpoint Investigation
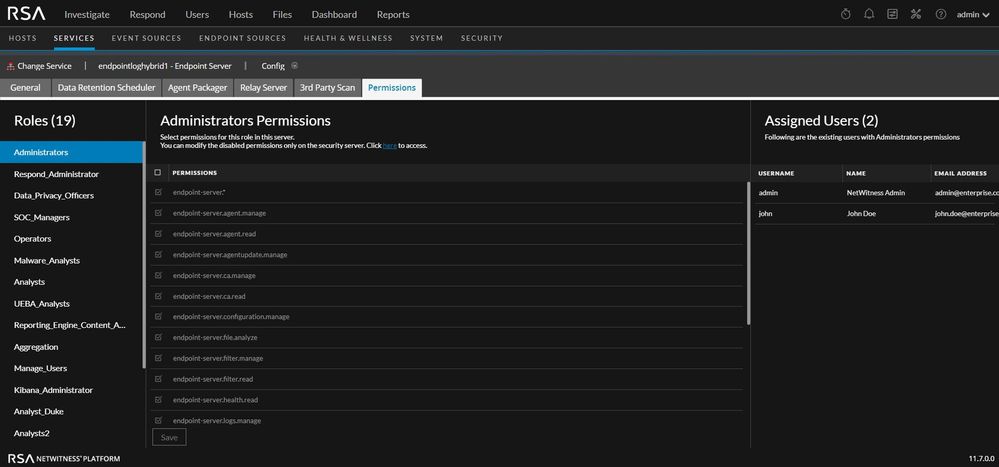
Granular Role Based Access Control for Endpoint Server
With the enhanced RBAC (Role-Based Access Control), administrators can grant or revoke access to specific Endpoint servers rather than all. And the addition of new permissions called endpoint-server.file.analyze and endpoint-server.tag.manage, adds flexibility in managing user privileges. For more information on managing permissions for an individual Endpoint server, see NetWitness Endpoint Configuration Guide.
Few Privileges Removed From endpoint-server.agent.manage And Added to endpoint-server.file.analyze
Analyze File, Save Local Copy and Scan with OPSWAT privileges are removed from endpoint-server.agent.manage and added to a new permission called endpoint-server.file.analyze. For more information see the System Security and User Management Guide.
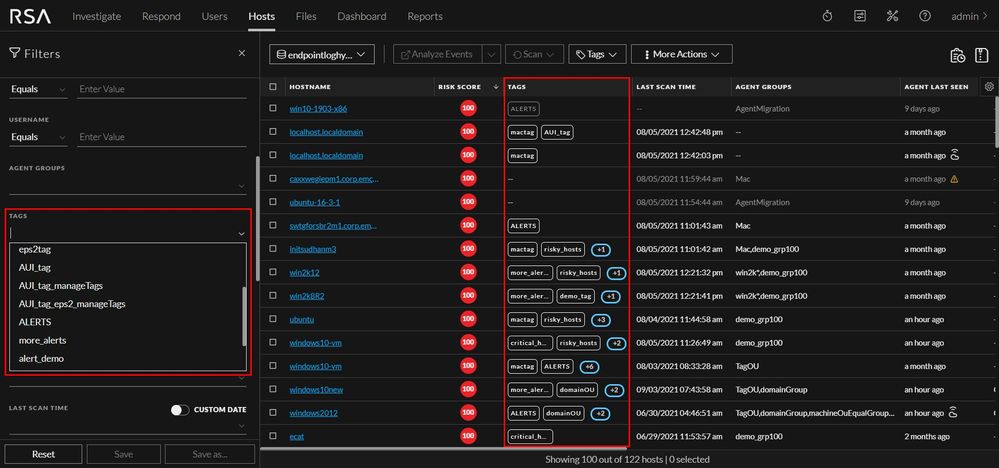
Manage Hosts Using Tags
Analysts can create Tags to manage the hosts. Tags are custom texts (can combine alphanumeric and special characters) that you can create and assign to hosts. You can create host groups based on tags, and on the Hosts view, you can filter hosts by tags using the filters pane. Administrators can create and assign tags while generating the agent packager, and these are added to the hosts by default when the Endpoint agent is installed. For more information on managing tags, see NetWitness Endpoint User Guide.
Enhanced Windows Agent to Support Detecting the Persistence Techniques Targeting the Registry
The enhanced Windows agents detects persistence techniques that use the Windows registry. The registry monitor is more reliable now as it detects suspicious activity in an enhanced manner. For more information, see the NetWitness Endpoint User Guide.
Enhanced Suspicious Thread Detection
This enhancement to the suspicious thread detection helps detect and report suspicious threads more effectively using different methods. This enhancement enables analysts to have access to all the details and capabilities related to the suspicious threads as before. For more information, refer NetWitness Endpoint User Guide.
Delete Blocked Files Through Elevated Command Prompt
You can delete the blocked files on the host using the delete command on the elevated command prompt on the host.
Concentrator, Decoder, and Log Decoder ServicesConcentrator, Decoder, and Log Decoder Services
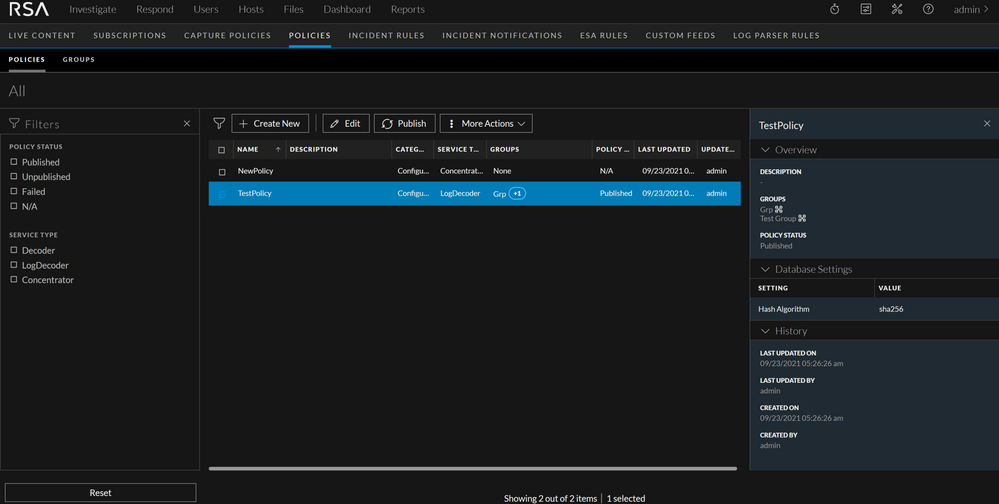
Introduction of Centralized Configuration Management
The management of general NetWitness core services namely Concentrator, Decoder, and Log Decoder configurations can be administered centrally from a single policy-based interface and distributed to multiple services. With centralized configuration management, administrators can:
-
Create a group of the same service type based on similar hardware profiles or other criteria
-
Add configuration items to policies in order to customize settings. Any settings which are not in the policy will be left as default
-
Apply customized settings to any number of services in one step
-
Restart all services within a group to apply changes
-
View when an action is required, such as service restart, unpublished policies or out-of-compliance services indicated by the icon.
-
Revert changes to a policy or group quickly
For more information, see Host and Services Getting Started Guide.
Enhanced Query Accuracy
An optional index configuration is available on a per meta key basis to extend the default key-value search into an N-gram layout. In addition to enabling query and reporting capabilities, this combination also provides complete and accurate search results, even if a maximum value threshold has been met.
For more information, see N-grams in the Core Database Tuning Guide.
Event Stream Analysis (ESA)Event Stream Analysis (ESA)
Enhancements for persisting Events and Incidents
Analysts can persist events encompassed in an incident, thus enabling to view the incident in the future, regardless of its age. Analysts can:
-
Pin or unpin multiple events at an incident and alert level
-
View details on when the events were persisted.
-
Check the status of the persisted events, whether it is Completed, Partial, or None.
-
Administrators can set up permissions for users to persist raw data associated with a particular incident.
For more information, see the Respond User Guide.
Platform Platform
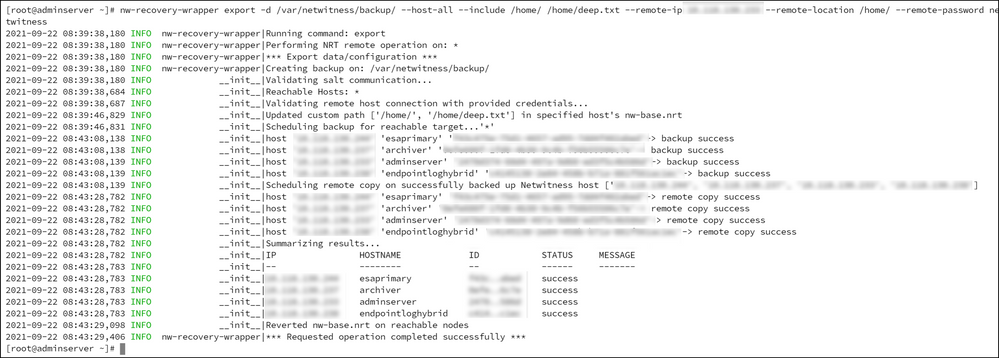
Backup and Restore Improvements
A new NetWitness Recovery Wrapper tool is introduced to centrally back up and restore individual or multiple hosts. This tool allows custom files to be incorporated in restorations and handles all supported deployment installations (Physical, Virtual, and Cloud).
With NetWitness Recovery Tool administrators can:
-
Back up (export) an individual, a specific, or all hosts at a time
-
Restore (import) an individual host at a time
-
Customize files or folders during backup and restore
-
Copy backup data to remote host location from NetWitness hosts and vice versa
For more information, see "Disaster Recovery (Back Up and Restore)" topic in the NetWitness Recovery Tool User Guide for NetWitness.
UpgradesUpgrades
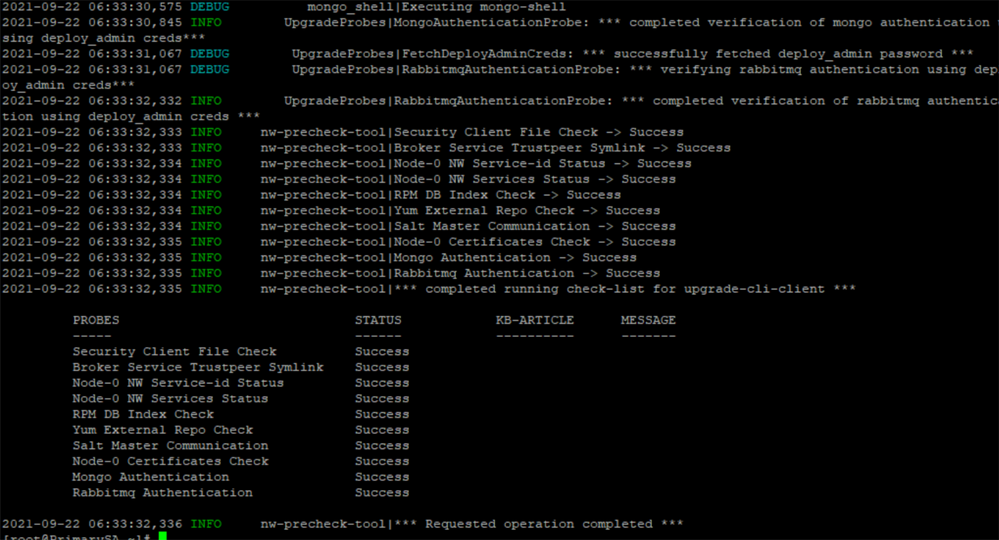
Introduction of Pre-Upgrade Check Utility
A new health-check utility is introduced for administrators to analyze the current NetWitness setup and identify conditions that may impact the upgrade. If any issues are detected, the issues can be resolved before proceeding with the upgrade.
The pre-upgrade check verifies the following:
-
Security Client File Check - Ensures security-client-amqp.yml file is not present
-
Node-0 NW Service-id Status - Ensures all the service-ids are intact with the services in Node 0
-
Broker Service Trustpeer Symlink - Ensures Broker symlink file (/etc/netwitness/ng/broker/trustpeers/) is not broken
-
Node-0 NW Services Status - Checks the status of all the services in Node 0
-
Yum External Repo Check - Ensures external repos are not available
-
RPM DB Index Check - Checks if the RPM DB is corrupted
-
Salt Master Communication - Verifies the salt communication from Node 0 to all the Nodes
-
Node-0 Certificates Check - Checks if any certificates are missing, expired, or invalid
-
Mongo Authentication - Validates the deploy_admin credentials fetched from security-cli-client using Mongo client
-
RabbitMQ Authentication - Validates the deploy_admin credentials fetched from security-cli-client using RabbitMQ
For more information, see Upgrade Guide for NetWitness 11.7.
NetWitness ServicesNetWitness Services
Introduction of NetWitness Service Topology Map
A view of the hierarchical layout of all NetWitness core services depicting the collection and aggregation of services provides administrators and analysts quick insights into their deployment and the services that are online or offline. This topology displays only the Broker, Concentrator, Log Decoder, Packet Decoder, Hybrids, and Log Collector services.
Note: Reporting Engine, Malware Analysis, UEBA, Endpoint Server, Cloud Link service, and Warehouse Connectors are not supported.